Comments
- No comments found

Blockchain is preventing potential fraud and reducing the chance of data being stolen or compromised.
As individuals, businesses, and governments lock themselves in a constant battle against fraud, bugs, and malicious actors, you can find hope of improvising cyber security with blockchain.
Blockchain technology is a distributed ledger, which eliminates the need for a third party organization, and makes use of a distributed database. This helps in lowering the transaction costs. Besides, third party organizations use a centralized database, which enhances the risk of fraudulent activity.
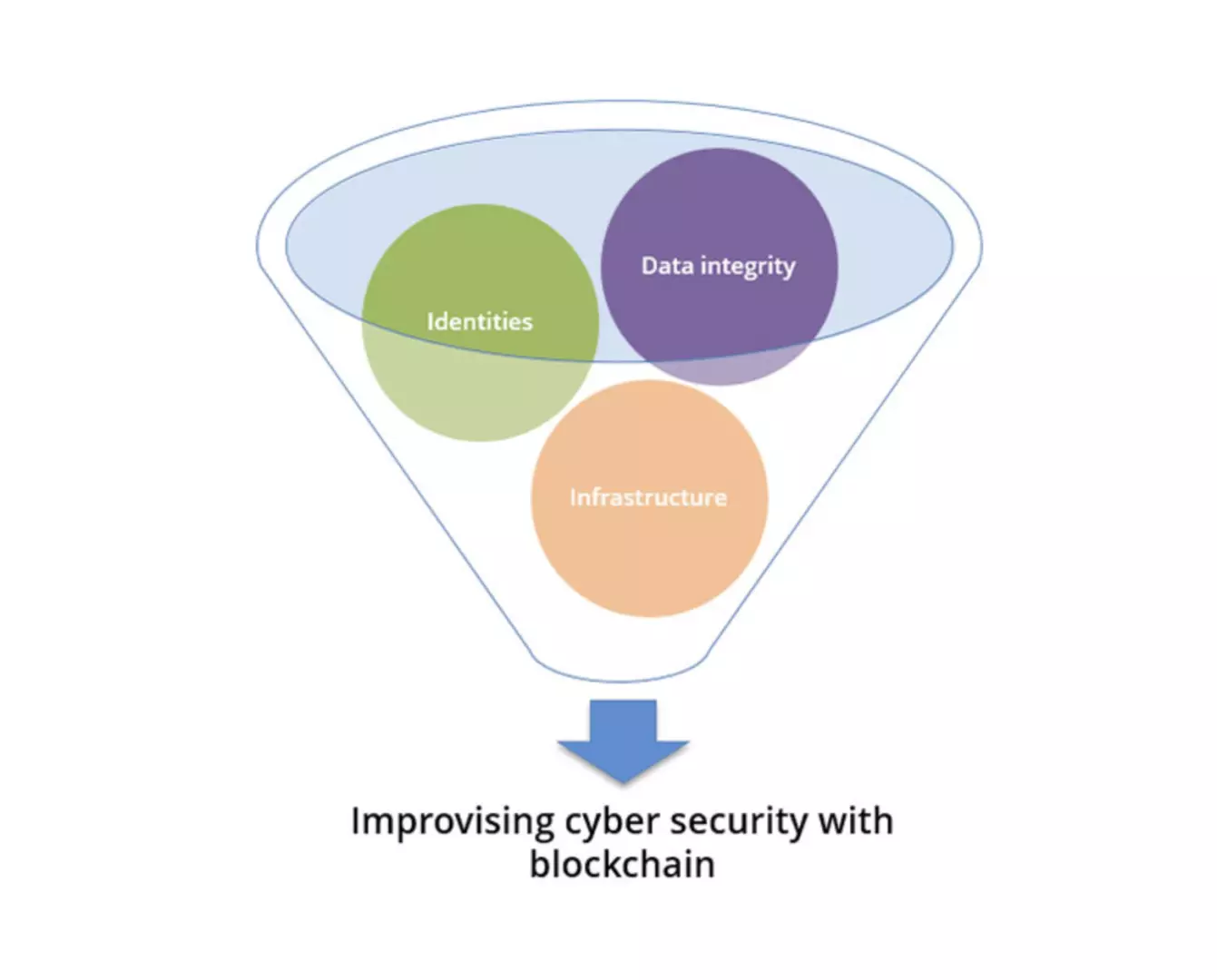
Just how blockchain has tracked, recorded, and secured transactions made within Bitcoin, it is in a position to defend many critical systems from cyber attacks that can be devastating. The need for improvising cyber security with blockchain emancipates from the fact that today, we are in a digital society. And in a digital society, if appropriate measures aren’t taken, both information and identity are at the risk of being attacked by criminals or inimical state actors.
There are three fronts in which the blockchains can increase cyber security – blocking identity theft, preventing data tampering, and stopping Denial of Service attacks. Here’s how.
One of the most popular forms of public key cryptography that help secure websites, emails, messaging apps, and other forms of communication, is the Public Key Infrastructure (PKI). The issue with this form of cryptography is that most implementations of PKI depend on the centralized and trusted third party Certificate Authorities (CA), which hackers can easily compromise and spoof user identities, cracking encrypted communications.
Instead, if keys were published on the blockchain, the risk of false key propagation would be eliminated. Moreover, blockchain enables applications to verify the identity of the people you are communicating. For example, Certain, which is an example of the first implementation of blockchain-based KPI.
Private keys are used for signing documents and files for recipients and users to verify the source of the data they are handling. And protecting these keys from tampering is difficult, especially if the key is meant to be a secret.
Therefore, blockchain replaces such secrets with transparency, when signing a document. The technology distributes evidence across many blockchain nodes. Such an arrangement makes it practically impossible to manipulate data without being caught. A data security startup, with the aim of replacing key-based data authentication, initiated a blockchain project called Keyless Signature Structure (KSI). On KSI are stored hashes of the original data on the blockchain. KSI also verifies other copies of files by running hashing algorithms and comparing results with what’s stored on the blockchain. As the original hash exists on millions of nodes, any manipulation of the data will be quickly discovered.
Frequent Denial of Service (DoS) attacks highlight how easy it has become for hackers to target critical services. The October DDoS attackers, for example, were able to cut off access to Twitter, Paypal, Netflix, and other services for several hours. This was also another manifestation of the failure of centralized infrastructures.
Blockchain technology overcomes this security issue while storing DNS entries, by removing the single target, which when attacked by the hackers, could compromise the entire system.
While the old threats linger, new and unexpected cybersecurity threats will continue to emerge. Blockchain will prove to be a powerful tool for experts and engineers to harden their systems against a plethora of threats that surround us. And this is especially true as far as centralized weaknesses and single points of failure are the concern.
Naveen is the Founder and CEO of Allerin, a software solutions provider that delivers innovative and agile solutions that enable to automate, inspire and impress. He is a seasoned professional with more than 20 years of experience, with extensive experience in customizing open source products for cost optimizations of large scale IT deployment. He is currently working on Internet of Things solutions with Big Data Analytics. Naveen completed his programming qualifications in various Indian institutes.
Leave your comments
Post comment as a guest