Comments
- No comments found

Organizations from SME to Enterprise are reviewing and modernizing their security strategies in a threat landscape that continues to dynamically evolve in scope, scale and sophistication, especially with the rapid advance of digital transformation from hybrid working, to Software-As-A-Service (SaaS) adoption and Bring-Your-Own-Device (BYOD) diffusion.
Resilience to vulnerabilities is an imperative and the focus is on exactly this – raising awareness to build resiliency – with the aim to help support organizations of any size in proactively enhancing their security posture. With the CSAM theme this year being: ‘It's Easy to Stay Safe Online - See Yourself in Cyber’ we will explore the key vectors of change impacting on Cyber Security today, with resources and tips on actions everyone can take to better negate the risk.
Cyber-attackers will always choose the path of least resistance. So, attention to security at the password level remains a key first step in keeping information safe – putting this into context, over 40% of breaches now involve stolen credentials with the number available on the dark web exceeding a staggering 24 billion! This was recently brought center stage by the extensive ripple effect caused by attacks on Uber, from logistical delays to customer dissatisfaction, through to lost driver income, and of course organizational costs from income to reputation, and ultimately trust. It is understood that the employee corporate credentials of an Uber EXT contractor were purchased on the dark web after their personal device had been compromised with malware. So, what can we learn from this?

Firstly, use unique, complex phrases for passwords with a mix of upper and lowercase letters, numbers and characters, and make sure to change this often, as recently discussed by Laura Shafer, Vice President of Product Marketing at 11:11 Systems. Additionally, using multi-factor authentication (MFA) and two-factor authentication (2FA) can make it harder for attackers to access your device, even if they have your login details. However, not all MFA approaches are made equal! For critical internal accounts within organizations, such as those of the C-Suite who are increasingly subject to attacks, the use of hardware tokens and FIDO passkeys is recommended.
This can especially increase resiliency to techniques such as phishing, to which some 89% of organizations have experienced an attack in the past year alone (HYPR 2022). With MFA or 2FA in place, it becomes much harder for attackers to create fake login pages to collect unsuspecting employee credential information, which appears to have been the case with Uber. Put simply, multi-factor authentication (MFA) is not optional anymore – it’s imperative - and beyond this it also heralds an acceleration in innovation and availability around passwordless Sign-Ins altogether.
Finally, and supporting the ever-present need to couple technology solutions with education and awareness, MFA Fatigue should also be acknowledged. These attacks involve the end user being bombarded with verification notifications and are reliant on their ability to approve a simple SMS, Voice or Push notification without having any context of the session they are actually authenticating. This also formed part of the Uber attack, in which MFA Fatigue combined with social engineering enabled its success – in this case the attacker posing as tech support via WhatsApp and telling the user to accept the MFA verification prompt. This naturally makes Social Engineering our next area of focus!

Employing psychological tricks that exploit vulnerabilities in how people react to specific situations and change their behaviours, social engineering attacks come in 5 core types, namely phishing, watering hole attacks, business email compromise (BEC), physical social engineering and USB Fraud. In 2021, more infections were caused by phishing attacks than any other vector. Innovation in areas such as Deepfakes, which employ AI technology to create fraudulent recordings, videos or images of real people, have made phishing attacks even more difficult to detect.
This attack vector is also a significant contributor to cloud security concerns. In the Foundry’s 2022 Cloud Computing Survey, some 35% of IT decision makers listed data privacy and security as their top cloud challenge. Additional research by Kaspersky Lab finds that around 33% of cybersecurity cloud incidents can be attributed to social engineering techniques. To address this, investment in zero-trust infrastructure can limit the potential damage of these and other threats, both internal and external to your organization. It also heightens focus on the benefits of Infrastructure as a Service (IaaS) platforms which bring together the need for security, agility, flexibility, visibility, and scalability, as exemplified by 11:11 Cloud.
Empowering and educating all staff, not just those in tech facing roles, is also key here – cybersecurity is a shared responsibility for everyone and support to enable this must be addressed across technology, culture, process and skills perspectives. This is especially true in around topics such as Social Engineering which absolutely preys on human nature and trust. As an example, how many people do you know who have received training in psychological manipulation as part of their organization onboarding process?
Probably not many…
Additionally, lapses in appropriate and effective vulnerability management are a leading concern, especially around levels of unpatched software. During the height of the pandemic, research showed many organizations were regularly delaying patch updates (IBM 2021) and now an additional study shows as many as 66% of organizations have a vulnerability backlog of an eye-watering 100K bugs! Reflecting back on the issues discussed related to passwords, this is another example of ensuring that basic cyber hygiene is embedded by design.

And beyond this, greater attention must be placed on testing. As an example, recent research by Noname Security shows a clear disconnect, or even a level of denial here, with just 11% of respondents testing APIs for signs of abuse in real-time - yet 67% stating they are confident that their DAST and SAST tools are capable of testing APIs. Validating the reality of disaster recovery is another area where extensive testing is essential. Recommendations include involving scenario- or event-based testing, even to the level of providing application testing and end-user testing in some cases to ensure a robust, well-planned and validated strategy.
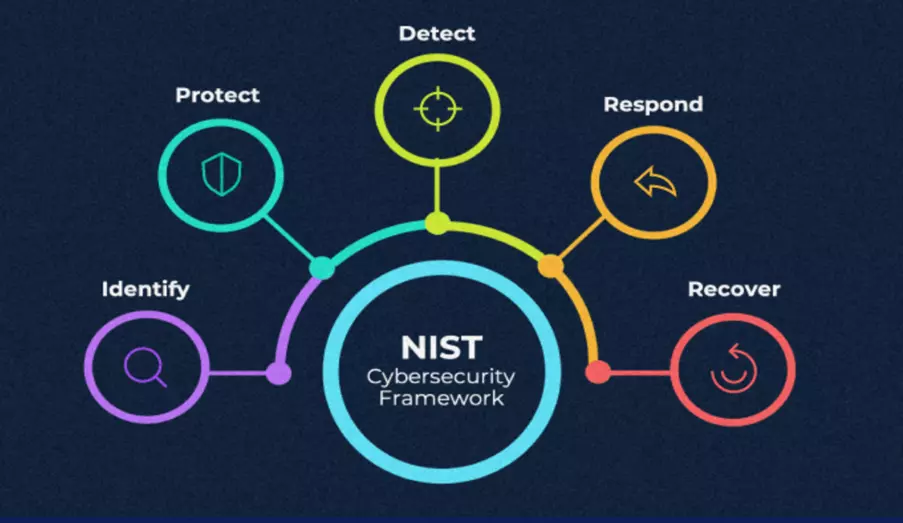
And finally, the NIST Cybersecurity Framework is highly recommended to help protect your business through shared best practice. Now downloaded over 1.7 million times, the framework outlines a strategy to better understand your organisation’s security risks, protect against them and, in the event of an attack, how to better triage, respond and recover. The framework holistically covers five core function areas – Identify, Protect, Detect, Respond and Recover. Putting this into context to highlight its real-world applicability, and taking Identify as an example, it is critical to know the who/what/where of your data storage, application and system links, role access and more.
Automation tools such as Continuous Risk Scanning can be very effective, helping to discover security vectors that were previously unknown, identifying the most significant risk areas, and ensuring you ‘get on the right path’ for enhanced protection and more active security intelligence. When we consider that half of all organizations have not put a cybersecurity risk plan in place, taking that first step today has never mattered more!
Cybercrime exists in a world of constant change and today’s surge in cybercriminal activity directly correlates to the increase in the attack surface. Last year alone, cybercrime rose more than 15% and so, it is abundantly clear that this focus has never been more important, and indeed must be an all year round imperative. A multi-layered approach to both proactive prevention and real-time response is key, combining automated protection and mitigation with a human perspective by design. To find out more about how 11:11 Systems supports Cloud, Connectivity and Security more information is freely available here.
All questions and feedback most welcome, Sally
Prof. Sally Eaves is a highly experienced chief technology officer, professor in advanced technologies, and a Global Strategic Advisor on digital transformation specializing in the application of emergent technologies, notably AI, 5G, cloud, security, and IoT disciplines, for business and IT transformation, alongside social impact at scale, especially from sustainability and DEI perspectives.
An international keynote speaker and author, Sally was an inaugural recipient of the Frontier Technology and Social Impact award, presented at the United Nations, and has been described as the "torchbearer for ethical tech", founding Aspirational Futures to enhance inclusion, diversity, and belonging in the technology space and beyond. Sally is also the chair for the Global Cyber Trust at GFCYBER.
Dr. Sally Eaves is a highly experienced Chief Technology Officer, Professor in Advanced Technologies and a Global Strategic Advisor on Digital Transformation specialising in the application of emergent technologies, notably AI, FinTech, Blockchain & 5G disciplines, for business transformation and social impact at scale. An international Keynote Speaker and Author, Sally was an inaugural recipient of the Frontier Technology and Social Impact award, presented at the United Nations in 2018 and has been described as the ‘torchbearer for ethical tech’ founding Aspirational Futures to enhance inclusion, diversity and belonging in the technology space and beyond.
Leave your comments
Post comment as a guest