Comments
- No comments found

In the digital age, cybersecurity is more important than ever.
As we rely more and more on technology to store and transmit sensitive information, the risk of cyber attacks grows. Cyber attacks can come from anywhere in the world, and they can be devastating for individuals and businesses alike.
I've recently interviewed Boaz Gelbord, Chief Security Officer at Akamai Technologies. In this article, we explore the ever-increasing threat of cybercrime in the digital age and discuss how organizations can stay ahead of these threats. During our discussion, Dr. Gelbord shared valuable insights on implementing a strategic approach to cybersecurity and building a stronger ecosystem through automation, analytics, and architecture. We also discussed the importance of resilience, fault tolerance, and inspection methods in surviving attacks.
Dr. Gelboard’s keynote speech at RSA Conference was also insightful, where he discussed the importance of automation, analytics, and architecture in cybersecurity. He explained how these three principles work together to improve security, and how organizations can evolve their analytics to keep pace with new threats. We examined the key findings of Akamai’s State of Internet report and identified potential vulnerabilities that organizations and individuals should be aware of. We also explored the strategies financial firms can adopt to mitigate the risk of DDoS and the significance of the collaboration between Akamai and FS-ISAC to the financial community.
If you are just starting to implement automation, analytics, and architecture in your security practices, Dr. Gelbord offered valuable advice that will help you get started. We wrapped up our discussion by discussing how cybersecurity is evolving in the digital age and the trends that Dr. Gelboard believes it will have the biggest impact.
Cybersecurity is essential for protecting sensitive information, such as personal and financial data, intellectual property, and confidential business information. Cyber attacks can result in stolen identities, financial loss, reputational damage, and legal liabilities. In some cases, cyber attacks can even lead to physical harm.
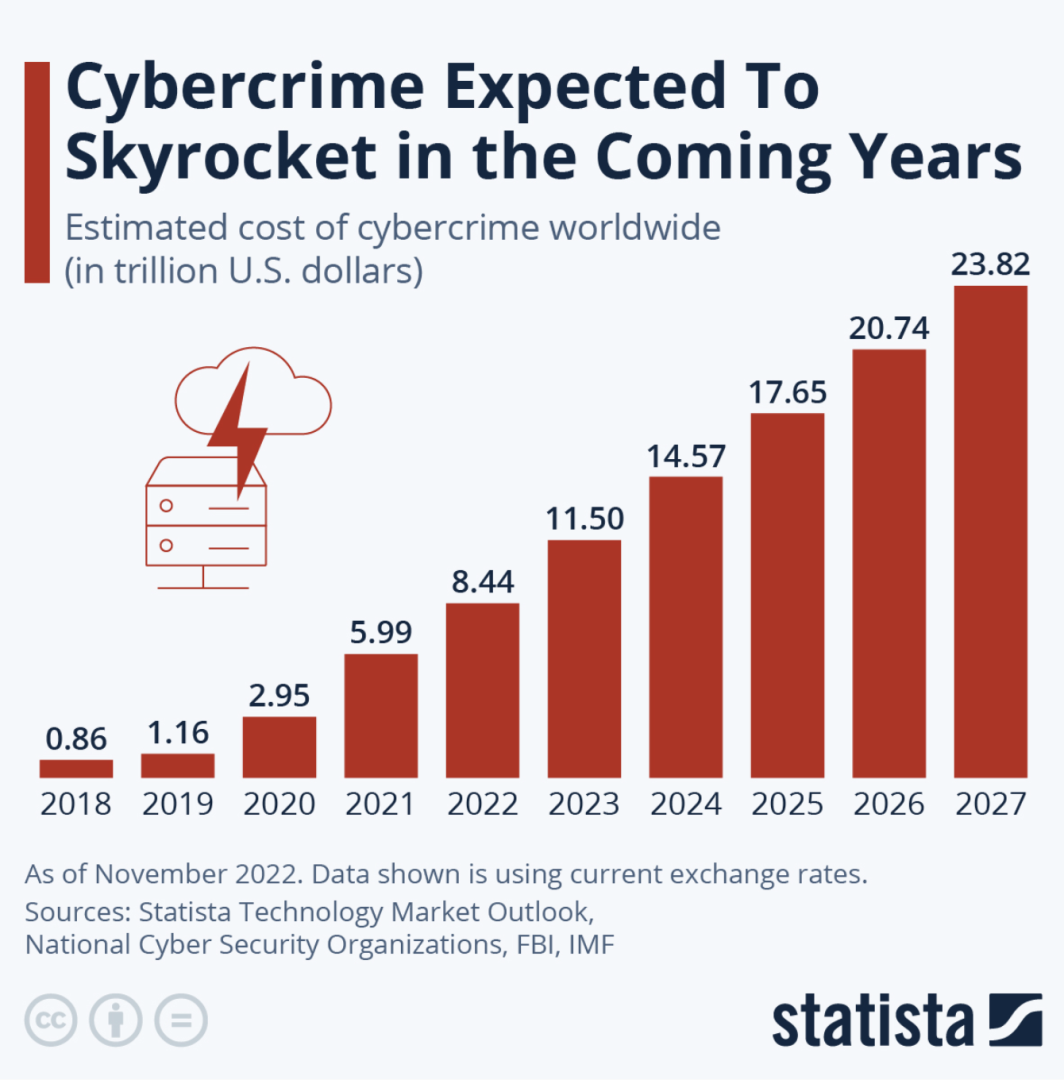
With the increasing amount of personal and sensitive information stored digitally, cybersecurity is crucial to prevent unauthorized access to this information. Cyber attacks can be costly and damaging to both individuals and organizations, as they can result in financial loss, reputational damage, and legal liabilities. Furthermore, the impact of a cyber attack can be far-reaching, affecting not only the immediate target but also their clients, customers, and business partners.
In recent years, there has been a surge in the number of cyber attacks, with hackers becoming more sophisticated and the methods they use more complex. It's not just large corporations that are at risk, either; small and medium-sized businesses, as well as individuals, are equally vulnerable to cyber attacks. In fact, smaller organizations may be more susceptible to attacks as they often have fewer resources to devote to cybersecurity.
As technology continues to advance, so too do the methods used by cybercriminals. This means that cybersecurity must be an ongoing effort, with regular updates to security measures and employee training to keep up with the latest threats. It's not enough to simply have antivirus software installed; organizations must take a comprehensive approach to cybersecurity that includes both technical and non-technical measures.
There are several types of cyber attacks, including phishing attacks, malware attacks, ransomware attacks, and distributed denial-of-service (DDoS) attacks. Phishing attacks are one of the most common types of cyber attacks, and they involve tricking people into revealing sensitive information, such as login credentials or financial data. Malware attacks involve infecting a device with malicious software, such as viruses, worms, or Trojans. Ransomware attacks involve encrypting a victim's files and demanding payment in exchange for the decryption key. DDoS attacks involve overwhelming a website or network with traffic to make it inaccessible.
There are several steps individuals and businesses can take to stay safe online.

One of the most important steps is to keep software up to date, as updates often include security patches that address vulnerabilities. Additionally, it's essential to use strong, unique passwords for each account and to enable two-factor authentication wherever possible. Avoid clicking on suspicious links or downloading attachments from unknown sources, and be cautious when sharing sensitive information online.
In the digital age, cybersecurity is more important than ever. Cyber attacks can come from anywhere and can cause significant harm to individuals and businesses alike. By taking steps to stay safe online, such as keeping software up to date and avoiding suspicious links, individuals and businesses can reduce their risk of falling victim to cyber attacks. It's essential to be vigilant and to take cybersecurity seriously in today's interconnected world.
As technology continues to advance, the threat of cyber attacks is likely to increase. It's therefore essential for individuals and organizations to stay ahead of the curve and continually update their cybersecurity measures to keep up with the latest threats. This may include using more advanced technologies such as artificial intelligence and machine learning to detect and prevent cyber attacks. Another major trend in cybersecurity is the shift towards a more proactive approach. Instead of simply reacting to cyber attacks as they occur, organizations are beginning to take a more proactive stance by identifying potential vulnerabilities and addressing them before they can be exploited. This includes regular security assessments and penetration testing to identify weaknesses and improve security measures.
Privacy concerns are also a growing issue in the digital age, with individuals and organizations becoming more aware of the importance of protecting personal data. As a result, there is likely to be a greater focus on data privacy and the implementation of stricter regulations and guidelines around the handling of personal information. Cybersecurity is becoming an increasingly important consideration in the development of new technologies. As the Internet of Things (IoT) continues to grow, for example, there is a need for robust security measures to protect the many interconnected devices and systems that make up this network.
Cybersecurity will continue to be a critical issue in the digital age, with new threats and challenges emerging all the time. It's essential for individuals and organizations to stay vigilant and keep up with the latest developments in cybersecurity to protect their data and systems from harm. By taking a proactive approach to cybersecurity and staying up to date with the latest trends and technologies, we can all play our part in creating a safer and more secure digital environment.
Helen Yu is a Global Top 20 thought leader in 10 categories, including digital transformation, artificial intelligence, cloud computing, cybersecurity, internet of things and marketing. She is a Board Director, Fortune 500 Advisor, WSJ Best Selling & Award Winning Author, Keynote Speaker, Top 50 Women in Tech and IBM Top 10 Global Thought Leader in Digital Transformation. She is also the Founder & CEO of Tigon Advisory, a CXO-as-a-Service growth accelerator, which multiplies growth opportunities from startups to large enterprises. Helen collaborated with prestigious organizations including Intel, VMware, Salesforce, Cisco, Qualcomm, AT&T, IBM, Microsoft and Vodafone. She is also the author of Ascend Your Start-Up.
Leave your comments
Post comment as a guest