Comments
- No comments found

We’ve all attended big events where security was tight. Maybe not White House level; but people scanned your ticket or personal invitation, another person checked your ID and a cadre of bystanders with headsets and dark glasses stood along the edge making sure the event went smoothly.
You stood in a sea of thousands trading great conversation and creating experiences. Your motivation was an unforgettable time to network, meet old friends and make a few new ones. This was the event of the year.
Welcome to edge computing. It is truly the next big “mega event” for CXOs and their teams leading them into the future.
Use cases will rise dramatically with more interaction, more people, more IoT devices, more data collection and more processing and analytics coming together at the edge.
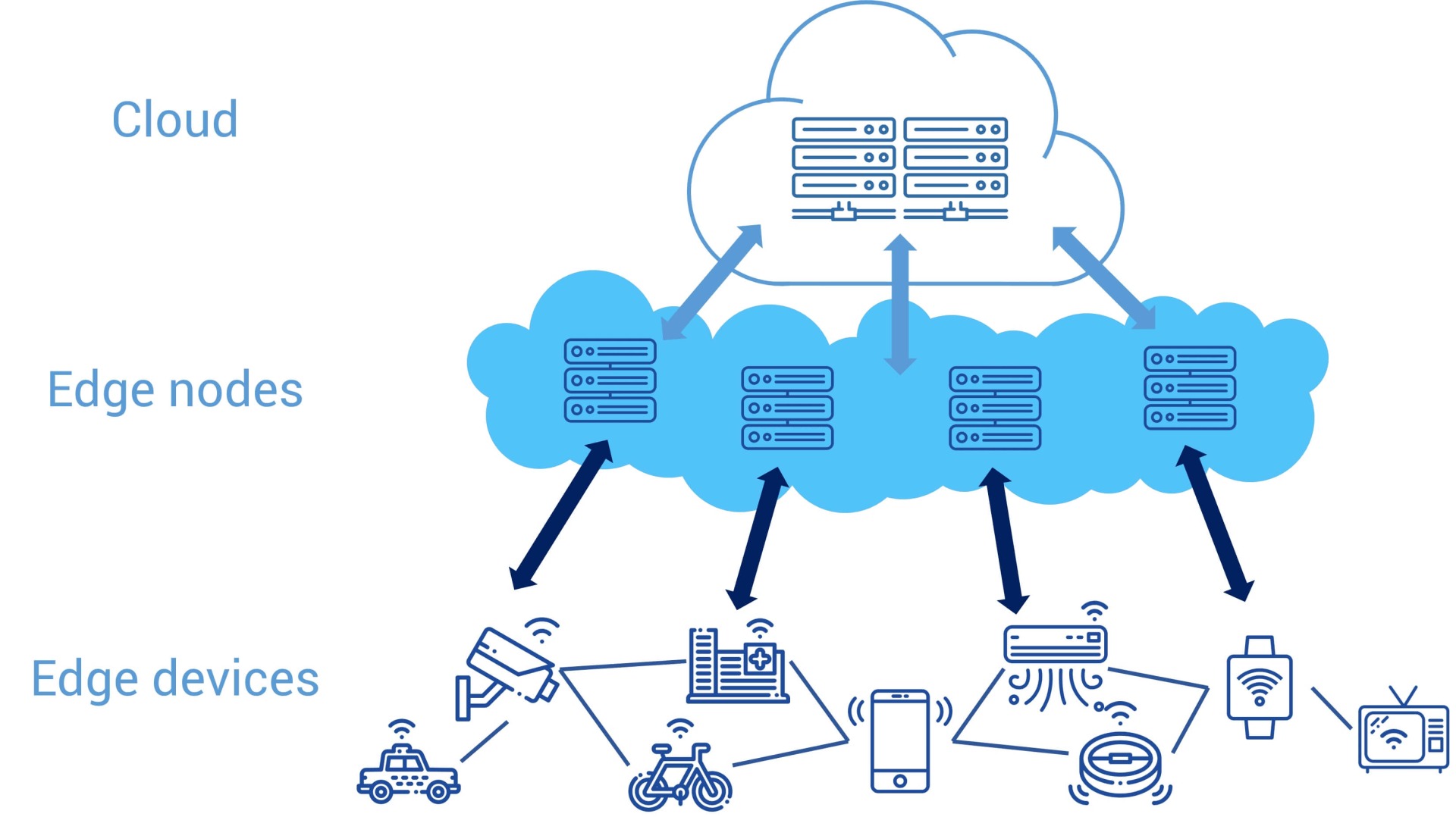
In its report entitled “Predicts 2022: The Distributed Enterprise Drives Computing to the Edge," Gartner forecasts that IoT units will grow with an 11% CAGR through 2030 – when there will be 500 billion connected devices. Data-heavy verticals like manufacturing, healthcare, oil and gas, transportation, public sector organization, and smart agriculture will grow even faster.
The significance of edge computing is about context
What I mean by context is a shift toward technology becoming agile, operating where and when the action is. Gartner’s report states: “The volume of data at the edge is massive and growing, requiring organizations to address it where it lives rather than send it all back to the core data center or cloud.”
The evolution toward edge computing is not just technology for technology’s sake. Distributed intelligence pushed to the edge solves critical problems like minimizing latency, improving bandwidth, and optimizing bandwidth usage and cost.
The significance of edge varies because edge is defined differently for each market sector. For example, edge for insurance might involve an IoT device alerting a policyholder of a water leak. The data (and I mean a lot of data) then originates from the device. While it’s cost prohibitive to send that data to the cloud, edge computing solves the problem because the location of the processing is in the device. For retail banking or healthcare, however, edge is completely different.
Here’s the list of priorities to consider from most important to least important: environment, understanding the role of cloud and edge computing, the computing infrastructure, data and transport of that data, security, and, finally, scalability.
Security at the edge puts you on the offense
Edge implementation for any organization will only be successful if a strategic cybersecurity approach is in place. To unpack this complex issue, AT&T has published the 42-page AT&T Cybersecurity Insights™ Report. A third in AT&T’s series on the topic, you’ll find questions to explore as you add edge to your technology stack and read about real use cases (the most helpful part of all).
Here are a few thought starters:
● How do you define edge in your market sector?
● What’s your approach to securing the edge?
● What framework will you use to assess your risk?
● What is the security maturity of your organization?
● Have you noticed other enterprises in your space adopting edge?
AT&T’s report found that perceived risk at the edge differs in each industry. Retail and energy and utilities are most concerned. Healthcare has the lowest perceived risk, although the report points out they are still above the midline. Finance and manufacturing cluster in the center with finance companies having the most experience, and thus maturity, with cybersecurity risk.
Exploring edge-to-edge solutions for specific industries is the key to delivering breakthrough customer experiences while keeping your business ahead of the digital curve. If you’re not sure where to start, AT&T has a helpful playbook talking about the “cyber scaries” .
While emerging technologies come with benefits, consider security first and foremost. Otherwise, your organization steps into reactionary mode. In fact, according to TechRepublic, 66% of IT teams view edge computing as a threat to organizations. Playing offense is your best strategy.
You’re invited.
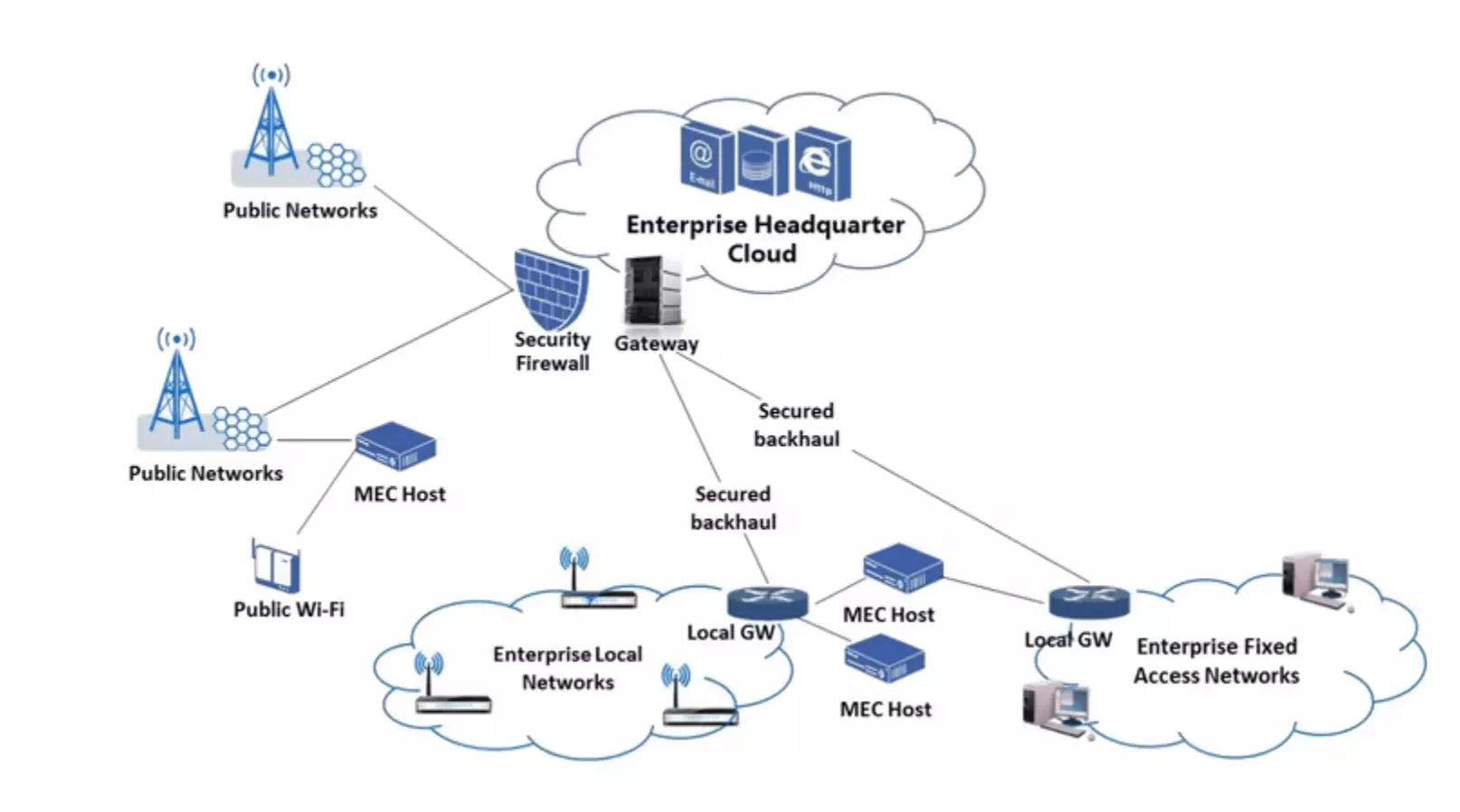
From Gartner’s report entitled “Tech Providers 2025: The Future of AI is on the Edge,” We see this prediction: "An ability to create AI-enabled outcomes across constrained compute ‘edges’ is the most impactful refactoring of value in technology markets since cloud computing. Product leaders must redistribute their products from the cloud to be closer to acquired event data to add value to customer processes." Edge computing, and making sure you have the right security around it, is fast becoming top of mind for every organization.
Think of edge computing as an invitation to the biggest event of the century. Everyone will be there. It’s where the action is. How will you ensure your data, customers, employees, devices, interactions and reputation are protected?
You don’t have to have all the answers. None of us do. Companies like AT&T are leading the way to filling the gaps. Because technology will never live up to its purpose if it doesn’t serve the greater needs of humankind. That’s the foundational principle for securing your world – and employing the right technology that moves people forward.
This article was sponsored by AT&T Business, but the opinions are my own and don’t necessarily represent BBN Times and AT&T Business’s positions or strategies."
Helen Yu is a Global Top 20 thought leader in 10 categories, including digital transformation, artificial intelligence, cloud computing, cybersecurity, internet of things and marketing. She is a Board Director, Fortune 500 Advisor, WSJ Best Selling & Award Winning Author, Keynote Speaker, Top 50 Women in Tech and IBM Top 10 Global Thought Leader in Digital Transformation. She is also the Founder & CEO of Tigon Advisory, a CXO-as-a-Service growth accelerator, which multiplies growth opportunities from startups to large enterprises. Helen collaborated with prestigious organizations including Intel, VMware, Salesforce, Cisco, Qualcomm, AT&T, IBM, Microsoft and Vodafone. She is also the author of Ascend Your Start-Up.
Leave your comments
Post comment as a guest