Comments
- No comments found

The widespread move to remote work during the Covid-19 pandemic created a number of cyber vulnerabilities.
Since most organizations rely on the internet; vulnerable data is now easily attainable.
No one can accurately predict when the server will be hacked, but it is still possible to prevent very unpleasant events.
In this article, we will provide 5 useful cybersecurity tips by introducing the concept of virtual data room to growth investors.
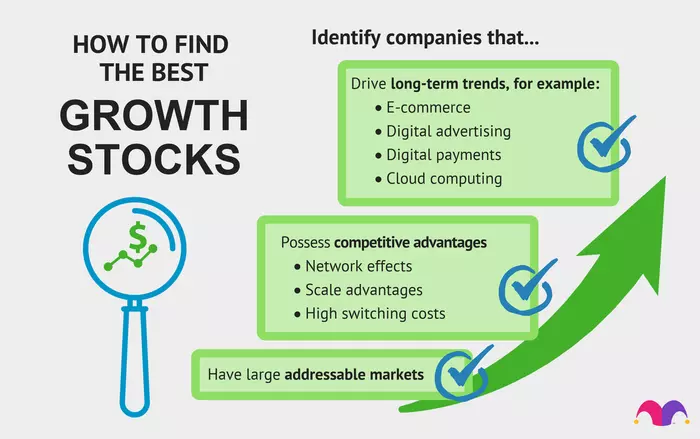
Growth investing is an investment strategy which focuses on increasing an investor's capital by buying promising stocks.
Most growth investors typically invest in growth stocks—which are startups or small companies whose earnings are expected to increase at an above-average rate compared to their peers.
Growth investing is attractive to many investors during the Covid-19 pandemic due to the impressive returns that have been generated by some rising companies.
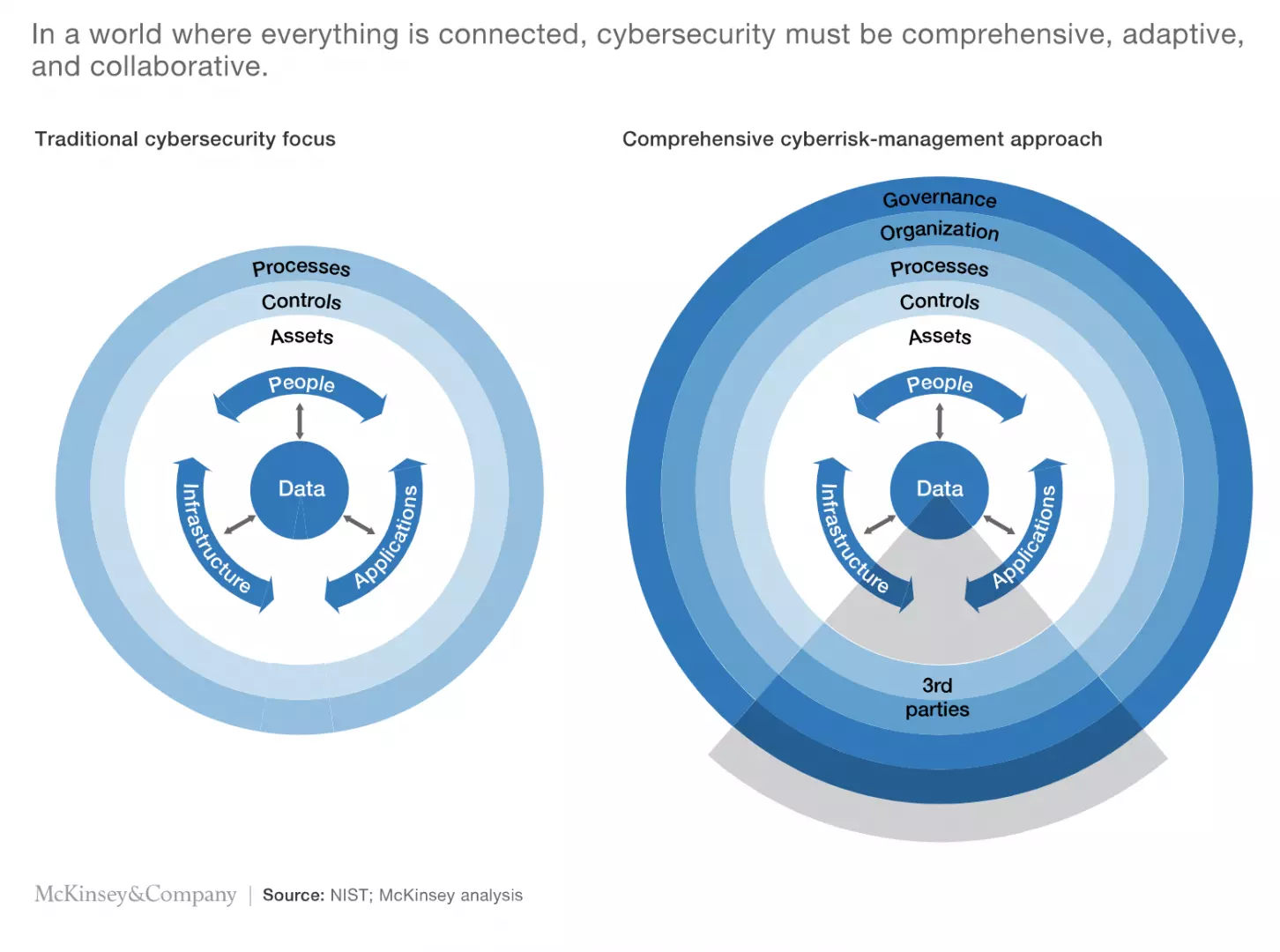
Cybersecurity and due diligence are now important factors when it comes to investing nowadays.
IT alone cannot tackle cybersecurity. A more collaborative approach to cyber risk is needed.
Worldwide IT spending will total $4.2 trillion by the end of 2021 (8.6% up on 2020), rising to $4.4 trillion in 2022.
Virtual Data Rooms (VDR) is a new technology for saving and sharing information.
The key features of electronic data rooms are:
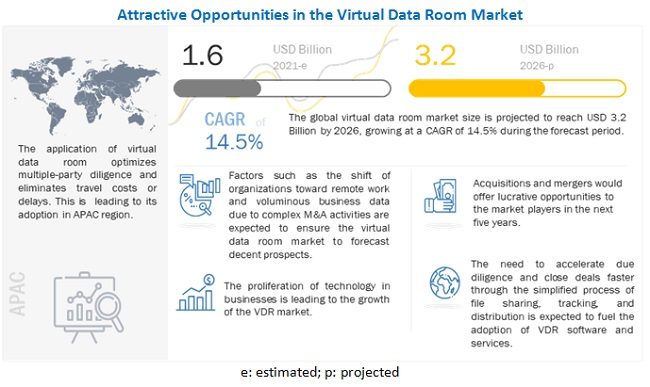
Source: Markets & Markets
According to a Forescout survey, 62% of corporations said their firms face severe cyber security risks when acquiring new businesses, and cyber risk is their top worry.
53% of their survey respondents highlighted cyber security and data breach risks as having almost compromised their M&A deal.
The issue is not limited to the M&A process. Organizations that have had data and security breaches lose money due to the loss of their reputation.
After Yahoo's earlier data breaches were uncovered, Verizon discounted its original purchase price of $4.8 billion, resulting in a $350 million loss in 2017.
As a result, it is advisable to use secure virtual data room software that offers the highest level of protection and eliminates the possibility of a data leak.

A virtual data room is an indispensable tool for controlling and safely sharing your confidential documents.
The best virtual data rooms can provide a safe environment in which to process files. They only enable authorized access and include anti-fraud and anti-hacking features to protect data from unauthorized access.
To protect your data, you can use these security virtual data room features:
Since most virtual data room services are used to communicate sensitive personal, financial, or classified information, access should only be allowed to a few people to avoid data breaches and leaks. These are the most prevalent qualities found in reputable data rooms.
Only one sign-in is required. Even if they engage in many projects, users may access their accounts using the same sign-in credentials.
Permissions can be set selectively. The data room administrator can choose which sections of documents are displayed to a specific user/group based on their participation in the process.
Verification in two steps. Logging in necessitates the usage of a password and a one-time code.
Permissions for individual documents can be customized. The administrator determines who has access to the system and what modifications they may make.
Restriction on time and IP address. The VDR can block particular IP addresses and limit access time to avoid intrusions.
Impersonation of a user's security. As the designated user, the administrator may guarantee that only the essential access is granted.
Reporting and recording of use. Internal audits and session records kept in milliseconds maintain track of any modifications made by users.
Virtual online data room software must adhere to a set of physical criteria to be secure, even if they are virtual. On-site security is just as critical as putting in place systems to protect internet data. These are some of them:
Dependable infrastructure components. In a fail-safe environment, quality hardware provides for 99.95 percent uptime.
Recovery from a disaster. Documents are almost disaster-proof when copies are kept in faraway data centers.
Data backup in real-time. An effective backup feature via an encrypted VPN link produces a duplicate of any uploaded document.
The data encryption feature uses many layers. Data integrity is improved by using high-grade encryption when transporting (TLS protocol) and storing (256-bit AES keys).
Protection of physical data. All data centers and power vaults are secured and monitored 24 hours a day, seven days a week, to maintain an uninterrupted workflow.
Several server locations are available. Disaster resilience is improved by having data centers in many locations.
Documents that end up in electronic data rooms aren't intended for everyone to view. VDR must-haves include the following options.
View from the fence. Side viewers, unlawful scanning, and photography are all protected by a barred screen view.
Various document access privileges are available. The user's role will determine what activities they can take with certain documents (download as a PDF file or encrypted copy, have editing rights, or restricted view, etc.)
Spreadsheet viewer that is safe to use. This provides for a secure view of data in Excel sheets and unique access settings.
Watermarking that changes over time. This feature encrypts access session information, including the user's IP address, access time, and date, in order to track data leaks.
No footsteps. It should be impossible to copy or save any document while viewing it on a device's browser history or memory.
Transparency allows virtual data room software users to obtain information based on their role in the transaction or organization. VDR administrators can use this type of control to allocate access to particular groups and redact documents in unique ways to the duties that each group is responsible for.
Look for a VDR that has a comprehensive role-based access control system that is easy to use for administrators. RBAC, for example, may assign a name to each action that occurs within the VDR right away. When a document is opened, the system keeps track of who did it.
Finally, find out if a data room provider’s software is easy to combine with your existing cybersecurity safeguards.
Even when the software featured customer-friendly, cutting-edge security capabilities, many researchers discovered that most organizations prefer not to leave cybersecurity measures solely in the hands of third-party software suppliers.
Instead, start with a thorough examination of your company's own data protection policies. Then look for virtual data room vendors that include the extra security features your scenario necessitates.
Leave your comments
Post comment as a guest