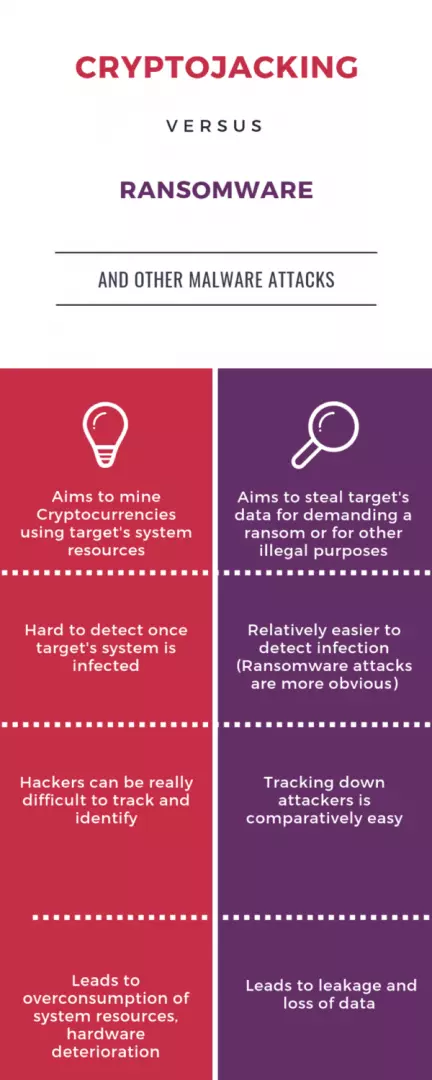
The growing adoption of blockchain and the seemingly continued bullishness of the cryptocurrency market has led to the rise of cryptojacking, which impacts the target’s processing capabilities, unlike other forms of cyber threats which impact the target’s data.
2021 saw the rise of ransomware as the biggest security risk faced by organizations and individuals alike. No network seemed secure enough from hackers who blocked people's access to their vital data and demanded money in exchange for relinquishing control of it. Many corporations were forced to hasten their efforts to revamp their security systems and invest in fortifying their IT infrastructure. While Ransomware wreaked havoc across the world, Blockchain technology continued its upward spiral of global acceptance and continued to be viewed as the foundation of a new world order based on a decentralized, digital means of monetary exchange - Cryptocurrency. Blockchain was also touted as the singular solution to nearly all security issues. Even the fearsome Ransomware could be rendered ineffective using Blockchain, by storing important data on multiple devices instead of a single location.
While Blockchain continued to wow the tech community with potentially revolutionary applications in data security and privacy, Cryptocurrency continued to make inroads in the financial world by becoming the most popular form of investment, and values soared. However, this seemingly perfect technology has also, in a way, become the cause of a new form of cybercrime - Cryptojacking. The continued, rapid rise of cryptojacking has not only posed a major hurdle in the worldwide adoption of cryptocurrencies, but has also overtaken Ransomware as the biggest cyber threat to corporations.
What is Cryptojacking?
Cryptojacking is a relatively new form of cyber attack where a hacker plants a malware on the target’s computer to mine cryptocurrency, usually the Cryptocurrency Monero, due to the anonymity it offers. As you might already know, cryptocurrency is mined by performing resource-intensive computations to contribute to the public distributed ledger, i.e., the blockchain. Thus, if a computer is being cryptojacked, it means the idle system resources (e.g., CPU, GPU, ASIC, etc.) are being used by remotely located hackers to mine cryptocurrency. It's as if you leave the key in your car at your workplace, and an unknown person uses it while you're working and returns it to its spot before you leave for home. If that becomes a recurring event, you’ll still possess your car, but will be losing more than you’re getting out of the car. You'll be paying excessively for fuel, your vehicle's components will be worn out faster than usual, and eventually, you'll end up having to perform major repairs or even buy a new vehicle much sooner than planned. Similarly, if your computer is cryptojacked and is used for mining for prolonged periods, you'll not only need to pay for power that you don't use but could also be forced to get new components or machines.
Why is Cryptojacking a Growing Worry for Businesses?
As even the most traditional businesses go digital, they become increasingly reliant on their computing devices. Whether we realize it or not, computers are becoming an essential part of organizations and are being employed for storing critical data, processing information, and automating tasks. There is also an increasing need to enhance the capabilities of these computing machines and maximizing their efficiency. As businesses attempt to scale their businesses, they need their IT infrastructure to be in the ideal condition to meet the changing demands. Under such circumstances, any loss in computing power leads to inefficiencies.
Cryptojacking usually attempts to target a large number of computers in an organization. So, when multiple computers in an organization are cryptojacked, the inefficiency is compounded, and even more so over time. The IT hardware belonging to an organization begins to lose its processing capability which leads to the need for frequent repairs and might lead to corruption of storage devices, potentially leading to a loss of valuable data - making it as bad or even worse than a Ransomware attack. While there is a chance of data recovery in case of a ransomware attack, if your storage devices get overworked due to continued cryptojacking, you may risk losing your data due to hardware failure.
Another big cause for worry is the fact that cryptojacking is easier to carry out than Ransomware attacks, as cryptojacking requires lower skill and scripts for mining cryptocurrencies and are easily available to everyone who seeks it. Additionally, cryptojacking programs run fairly undetected on computers, as opposed to Ransomware, which essentially announces itself to users to demand money. Thus, detecting cryptojacking attacks can be difficult, and even more so when the infected network consists of numerous devices and terminals, such as in large-scale enterprises. The longer an enterprise is subjected to cryptojacking, the worse off it will be after the attack.
How Can Businesses Protect Themselves From Cryptojacking?
Cryptojacking attacks, just like Ransomware and most other cyber threats, mainly materialize due to the carelessness of users in distinguishing between good and bad links and applications. Cryptojacking often begins with an unsuspecting user clicking on a link sent by hackers, disguised as trustworthy sources. The link, when clicked on, plants a mining script on the target's computer that surreptitiously runs in the background, mining cryptocurrency using the system's spare resources. Another method is by having mining scripts planted on websites receiving heavy traffic. While the users browse the website, the mining script uses system resources to mine cryptocurrencies. This may not impact an individual user too much, but the usual targets for cryptojacking are groups of users working for large organizations. To mitigate the parasitic action of cryptojacking on their IT infrastructure, technology and security leaders can take a couple of preventive steps as follows:
- Making employees aware of cryptojacking: Since the biggest vulnerability that leads to cryptojacking is human error and negligence, it only makes sense to initiate the countermeasures to cryptojacking by addressing that aspect. Employees, both technical and non-technical, should be made aware of cryptojacking and its severity. They should be educated as to how these attacks are carried out by hackers and how to identify such attempts.
- Installing adequate security measures: Organizations should invest in ad-blockers and anti-cryptojacking software for all their terminals, because when it comes to cryptojacking, being aware may not be enough. Most new antivirus software come with cryptojacking protection, which can help in identifying and eliminating hidden mining scripts. Security leaders should ensure that their network security solutions include anti-cryptomining extensions.
Every new system or technology, no matter how perfect it may seem at first, brings with it its own set of associated challenges. A good example of this is the rise of cryptojacking, a cyber threat that has emerged due to Blockchain, a technology that has become synonymous with privacy and security. While the risks posed by cryptojacking are undeniable and must be taken seriously by organizations both big and small, it should not blind us from viewing the revolutionary benefits of Blockchain, nor should it discourage businesses from investing in a future based on the technology.



Leave your comments
Post comment as a guest