Comments
- No comments found

Biometrics provide organizations a secure way to access and safeguard sensitive data.
Organizations are using biometrics technology in many ways.
Biometrics refers to the identification of individuals based on their unique physical or behavioral characteristics.
In the context of cybersecurity, biometrics can be used to authenticate a user's identity before granting access to sensitive information or systems. This can be more secure than traditional forms of authentication, such as passwords, which can be easily guessed or stolen.
There are several ways that businesses can improve their cybersecurity through the use of biometrics:
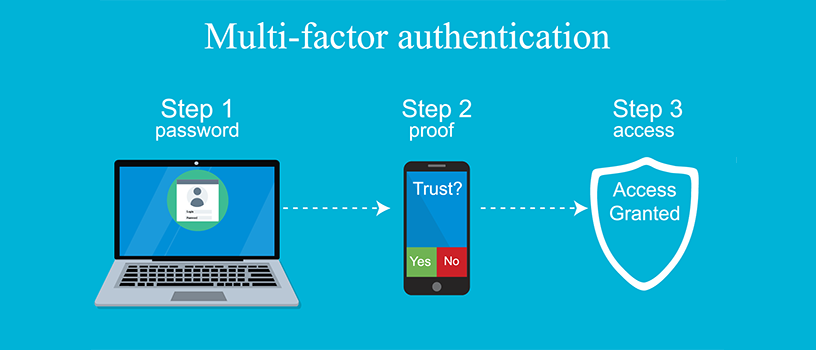
Multi-factor authentication (MFA) is a method of authentication in which a user is required to provide two or more forms of identification before being granted access to a system or information. The goal of MFA is to make it more difficult for unauthorized individuals to gain access to sensitive information or systems by requiring multiple forms of verification.
There are several types of factors that can be used for authentication:
Knowledge factors: These are things that a user knows, such as a password or a personal identification number (PIN).
Possession factors: These are things that a user has, such as a security token or a phone that receives a one-time passcode.
Inherence factors: These are things that are unique to a user, such as a fingerprint, facial recognition, or voice recognition.
MFA can be implemented in a variety of ways. One common example is the use of a password and a security token. A user would first enter a password and then enter a one-time passcode generated by a security token. Another example is using a password along with facial recognition or fingerprint scan.
MFA can provide a higher level of security compared to using single-factor authentication, such as a password alone, because it makes it more difficult for an attacker to gain access to a system or information. Even if an attacker is able to guess or steal a password, they would still need access to the other forms of verification in order to gain access.
It's important to note that MFA can also be implemented via a mobile app, using an authentication app, such as Google Authenticator or Microsoft Authenticator. They can be used to generate time-based one-time passwords (TOTP) that are combined with the password to complete the second factor of the multi-factor authentication process.
It's also important to state that while MFA increases security, it also adds complexity, so it's essential to choose a balance between security and user experience. Keep in mind that MFA systems can be bypassed, so it's important to have security measures in place to detect and respond to suspicious activity.
By requiring multiple forms of authentication, such as a password and a fingerprint, businesses can make it much more difficult for attackers to gain access to their systems.

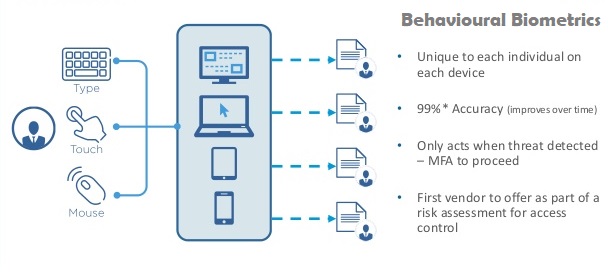
Behavioral biometrics refers to the identification of individuals based on their unique behavior patterns. These patterns can include things like the way a person types on a keyboard, the way they move their mouse, or the way they hold their phone. By analyzing these behavioral patterns, it is possible to create a unique profile for each individual, which can be used to authenticate their identity.
One way that behavioral biometrics can be used in cybersecurity is through continuous authentication, which involves monitoring a user's behavior in real-time to detect any anomalies that may indicate an attempted intrusion. For example, if a user's typing rhythm suddenly changes or their mouse movements become erratic, this could indicate that someone is trying to gain unauthorized access to their account.
Another way that behavioral biometrics can be used is by creating a unique "fingerprint" for each user based on their behavior patterns. This fingerprint can be used to authenticate a user's identity when they attempt to access a system or information. This method is useful for online services such as banking or e-commerce that can not use other biometrics such as fingerprints or facial recognition.
Some examples of behavioral biometrics that can be used for authentication include:
Keystroke dynamics: Analyzing the timing and rhythm of a user's keystrokes to create a unique profile
Mouse dynamics: Analyzing a user's mouse movements, including things like clicking speed, pressure, and movement patterns
Device fingerprints: Analyzing a user's device and network characteristics, such as IP address, browser version, and screen resolution to identify a unique signature
Speech Recognition:: Analyzing speech features such as pitch, rhythm, speaking speed, and word choice to create a unique profile
Behavioral biometrics can provide a high level of security, as it is difficult for an attacker to replicate the behavior patterns of an authorized user. Additionally, it allows the system to continuously monitor a user's behavior, so any suspicious activity can be detected and responded to in real-time.
However, it's also important to note that Behavioral biometrics is still a relatively new area of research and its implementation can raise some concerns. These include privacy, accuracy, and bias. It's important that the technology is transparent, user-centric, and has proper procedures for collection, storage, and use of the data.
By analyzing a user's behavior, such as the way they type or use a mouse, businesses can detect anomalies that may indicate an attempted intrusion.
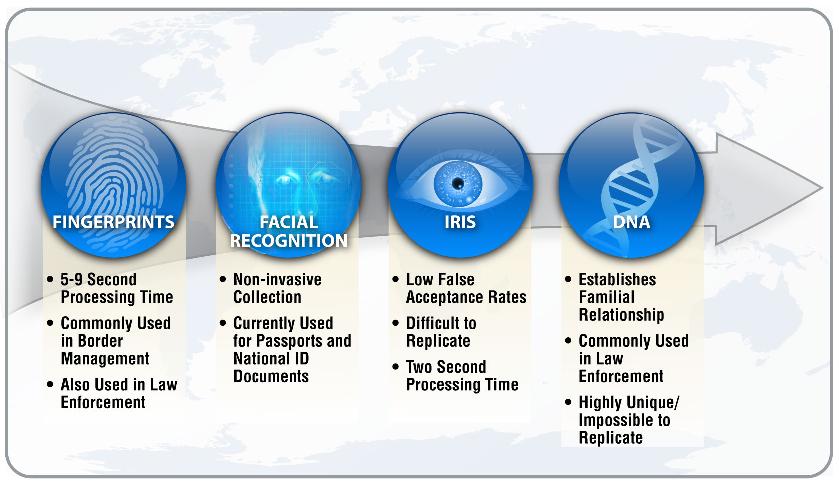
Biometric security systems are systems that use biometrics to authenticate a user's identity before granting access to a physical building, a device, or a sensitive area. These systems can be used to control access to a variety of different areas, including office buildings, data centers, and secure facilities.
There are several different types of biometric security systems, including:
Fingerprint scanners: This technology uses a person's unique fingerprint to authenticate their identity.
Facial recognition systems: This technology uses a person's unique facial features to authenticate their identity.
Iris recognition systems: This technology uses a person's unique iris pattern to authenticate their identity.
Hand geometry systems: This technology uses the shape of a person's hand to authenticate their identity.
Voice recognition systems: This technology uses a person's unique voiceprint to authenticate their identity.
The goal of these systems is to make it more difficult for unauthorized individuals to gain access to a physical building, device, or sensitive area by requiring a unique physical characteristic for authentication.
Biometric security systems can provide a high level of security, as it is difficult for an attacker to replicate the unique physical characteristics of an authorized user. Additionally, because biometric data cannot be easily lost, stolen, or forgotten like a password or card, it reduces the risk of unauthorized access.
On the other hand, it's also important to note that these systems can raise concerns about privacy, security and bias.
Privacy concerns may arise if biometric data is collected, stored, or shared without the consent of the individuals involved.
Security concerns may arise if the biometric data is hacked or stolen.
Bias concerns may arise if the biometric data is collected and stored in a way that discriminates against certain groups of people.
It's essential that these systems are implemented in a transparent and user-centric way, and that proper procedures are in place for the collection, storage, and use of the data. It's also important that these systems are integrated with other security measures such as intrusion detection systems, cameras, and other access control mechanisms.
Businesses can use biometric security systems, such as fingerprint scanners or facial recognition software, to control access to physical buildings or devices.
It's important that biometric-based password management systems are implemented in a transparent and user-centric way, and that proper procedures are in place for the collection, storage, and use of the data. Additionally, it's essential that these systems are integrated with other security measures such as intrusion detection systems, cameras, and other access control mechanisms to provide an overall robust security system.
It's more important than ever for businesses to leverage biometrics because cyber attacks are becoming more sophisticated and more frequent. Passwords can be easily guessed or stolen, and with the increasing number of devices and services that require authentication, it's becoming more difficult for users to remember unique and secure passwords for each one. Biometrics offer a more secure and convenient way to authenticate users and protect sensitive information.
While biometrics is a more robust security method it's not foolproof, as biometric data can also be compromised. It's important for companies to ensure that biometric data is stored securely and that employees are aware of the importance of protecting their biometric data.
Leave your comments
Post comment as a guest