Comments
- No comments found

In an era defined by technological innovation, artificial intelligence (AI) stands out as a transformative force.
From personalized recommendations to autonomous vehicles, AI's potential seems limitless. As organizations increasingly rely on AI to enhance their operations, they must also address a critical concern: cybersecurity. This article explores the intersection of AI and cybersecurity and offers insights into safeguarding your AI infrastructure in a rapidly evolving digital landscape.
AI has brought remarkable advancements to various industries, but it also presents new cybersecurity challenges. Machine learning algorithms, while powerful, can be vulnerable to attacks. Cybercriminals can manipulate data or inject malicious code, potentially compromising the integrity and confidentiality of AI systems.
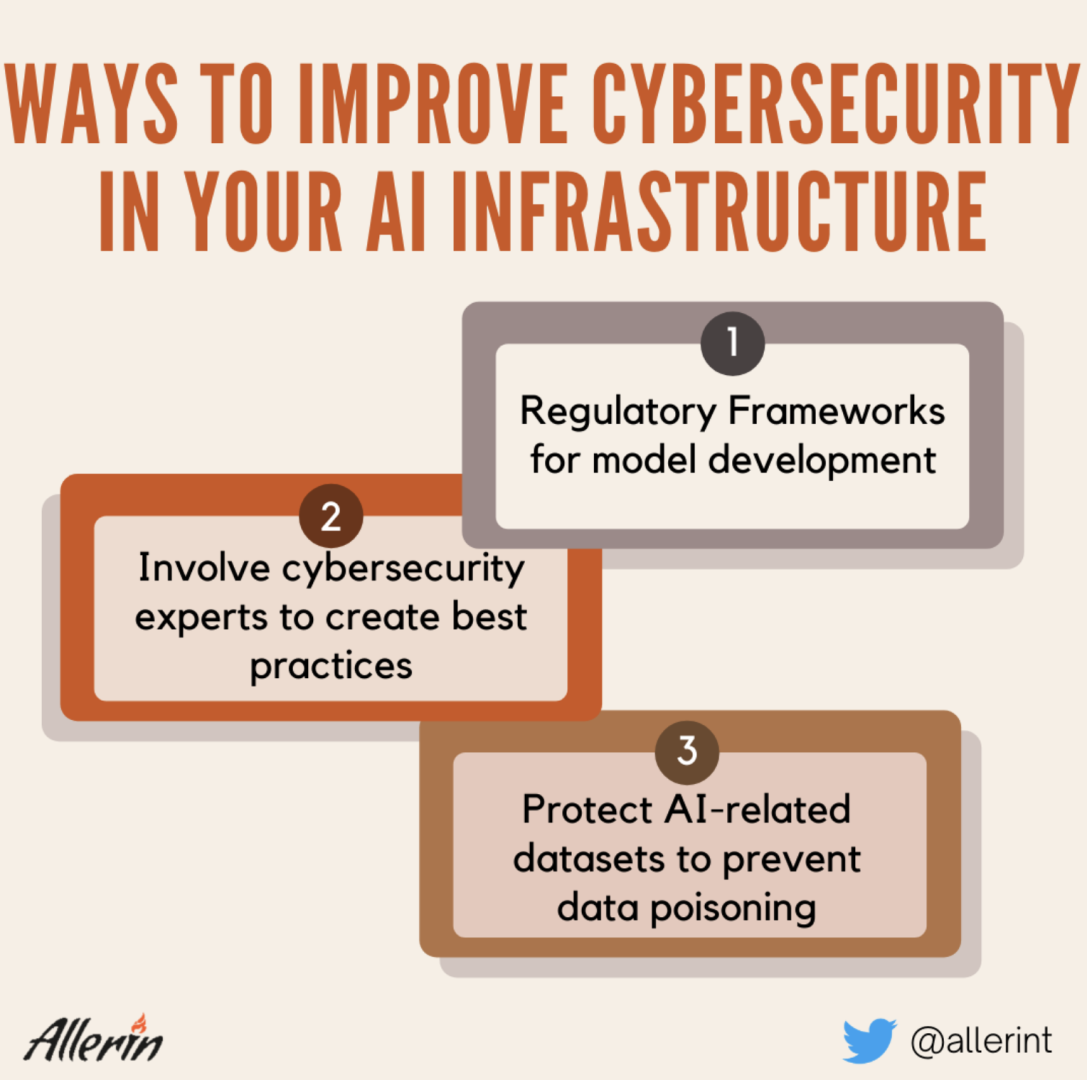
Cybersecurity begins with a solid foundation. Ensure that your AI infrastructure is built on secure principles from the ground up. Collaborate with cybersecurity experts to conduct threat assessments, identify potential vulnerabilities, and implement robust security measures.
Data is the lifeblood of AI. Protecting data is crucial to AI security. Employ encryption, access controls, and data anonymization techniques to safeguard sensitive information. Regularly audit data handling practices to maintain compliance with data protection regulations.

Traditional network security models may not be sufficient for AI environments. Adopt a Zero Trust Architecture (ZTA) approach, which requires verification from anyone trying to access resources, even if they are inside the organization's network. ZTA minimizes the risk of unauthorized access to AI systems.
Deploy advanced monitoring and anomaly detection tools that can identify unusual behavior within AI systems. AI-powered cybersecurity solutions can analyze vast datasets in real time, quickly flagging any deviations from normal operations.
Cybersecurity threats are constantly evolving. Keep AI frameworks, libraries, and software up to date with the latest security patches. Automated patch management systems can help ensure timely updates across your AI infrastructure.
Human error remains a significant cybersecurity risk. Educate your team about AI security best practices and the potential risks associated with AI systems. Promote a culture of cybersecurity awareness and vigilance.

Implement MFA for accessing AI systems and sensitive data. This additional layer of security ensures that even if login credentials are compromised, cybercriminals cannot gain unauthorized access.
Leverage AI's own capabilities for threat detection. AI-driven cybersecurity solutions can identify patterns and anomalies that may be indicative of cyberattacks. These systems can respond rapidly to mitigate risks.
Conduct regular security audits and penetration testing to assess the resilience of your AI infrastructure. These tests simulate real-world attacks, helping you identify weaknesses and improve your defenses.
Cybersecurity is a collective effort. Collaborate with industry peers, share threat intelligence, and stay informed about emerging threats and vulnerabilities. This collaborative approach strengthens the cybersecurity ecosystem.
Prepare for the possibility of a cybersecurity incident. Develop a comprehensive incident response plan that outlines roles, responsibilities, and procedures for addressing breaches. Regularly test and update this plan to ensure its effectiveness.

Stay informed about relevant data protection and cybersecurity regulations in your industry and region. Compliance with these regulations is not only a legal obligation but also a crucial component of AI security.
As AI continues to revolutionize industries, the importance of cybersecurity cannot be overstated. Protecting your AI infrastructure is not just a matter of compliance; it's a fundamental necessity for preserving trust and ensuring the reliability of AI systems. By adopting a proactive and comprehensive cybersecurity strategy, organizations can harness the full potential of AI while safeguarding against evolving cyber threats. The future belongs to those who combine innovation with unwavering security.
Naveen is the Founder and CEO of Allerin, a software solutions provider that delivers innovative and agile solutions that enable to automate, inspire and impress. He is a seasoned professional with more than 20 years of experience, with extensive experience in customizing open source products for cost optimizations of large scale IT deployment. He is currently working on Internet of Things solutions with Big Data Analytics. Naveen completed his programming qualifications in various Indian institutes.
Leave your comments
Post comment as a guest