From big players to SMBs, every organization has faced the impact of cyber threats at some point.
But, the new generation of automated cyber attacks will affect multiple businesses to an unimaginable extent.
With the onset of the digital age, going online became a necessity for every business. Most business processes, data storage, and data exchange are now handled digitally. Data has become such a significant asset that companies have started monetizing their data. Just like businesses, hackers also realized the potential of acquiring such critical data. Hence, cyber attackers have been utilizing different techniques such as brute-force attacks and malware to gain access to various networks and computers. Cyber attacks are so commonplace now that every 39 seconds, hackers attack a computer in the US. Cybersecurity experts are constantly trying to create prevention and mitigation strategies for several existing cyber threats and to discover new security loopholes to stay ahead of cyber attackers.
To improve security standards, they are also leveraging machine learning and artificial intelligence to identify new malware and detect malicious behavior in company networks. The advent of modern technologies such as IoT is exponentially increasing the number of connected devices to the extent that there was around 200 billion connected devices in 2020. Hence, cybersecurity professionals are adapting their systems to secure the increasing number of connected devices. However, just like cybersecurity experts, cyber attackers too are working on their techniques and knowledge. Hackers can now utilize artificial intelligence and machine learning to trigger automated cyber attacks that can easily compromise secure systems without any human intervention. Such automated cyber attacks pose an unprecedented level of cyber threat for organizations.
The Current State of Cyber Threats
Cyber threats have been troubling businesses and internet users for years. Currently, none of the big players in any industry are safe from data breaches. Even after deploying state-of-the-art security measures, multiple businesses have faced high profile security breaches. This epidemic of data breach has compromised the confidential data of millions of users and damaged the reputation of several industry giants. Hence, cybersecurity professionals are trying to find fail-safe solutions for data breaches.
Ransomware is a cyber threat for several businesses. Attackers infiltrate the system of the target organization and encrypt all their critical data. Then, they demand a ransom in exchange for decrypting the data. As a result, businesses can lose millions of dollars in ransom and infrastructure recovery. For example, the city of Atlanta was attacked using the infamous SamSam ransomware. The attackers asked for a ransom of $51,000. However, the impact of SamSam ransomware was so immense that the city of Atlanta was offline for five days. As a result, several significant citywide operations were halted. The total recovery cost after this attack was around $17 million. Reports suggest that such ransomware attacks are only going to increase in number leading to further losses for multiple businesses. Also, some western countries are accusing eastern nations of backing high profile cyber attacks that are apparently knocking down government and private infrastructure in western countries. Such allegations introduce a whole new angle of cyber warfare on a global scale.
The New Wave of Automated Cyber Attacks
Currently, cybercriminals have to constantly work on developing malware and malicious codes, along with months of planning. But, the discovery of automated cyber attacks will reduce the workload and enable easier execution of sophisticated cyber attacks. Such automated cyber attacks can include:
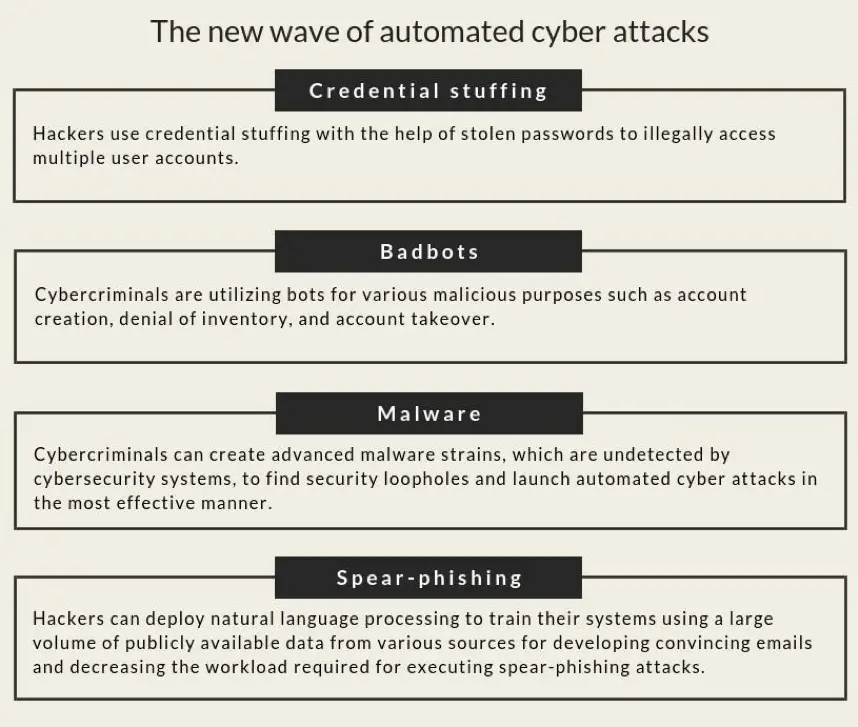
1. Credential Stuffing
Several users reuse their passwords for multiple online accounts. Such passwords and email addresses are compromised during high profile data breaches and sold on the dark web. Using such stolen passwords, attackers can implement credential stuffing. In credential stuffing, hackers utilize botnets for automated cyber attacks that attempt to hijack user accounts with the help of stolen credentials. Such attacks can lead to business losses due to fraud, network downtime, and system remediation.
Credential stuffing is primarily used to target businesses in the financial and retail sectors. For example, a UK bank reported a data breach that affected some of their customers’ sensitive information, such as account numbers, account balance, transaction history, contact details, and personal information. Such automated cyber attacks will be more common in the future. Attackers can also leverage machine learning to predict any user’s password based on their other passwords. With such immense potential, we might be looking at a future where if some passwords of any user get leaked online then all of their online accounts will be vulnerable to automated cyber attacks, forever.
2. Bad Bots
Bots have helped organizations automate workflows and tasks such as answering customer queries, managing leads, and promoting content. However, cybercriminals are utilizing bots for various malicious purposes such as fake account creation, denial of inventory, and account takeover.
Bots can deliver brute-force attacks to attempt illegal account log-ins. Also, bots can create multiple fake accounts to spread online propaganda. Besides, cybercriminals are using ‘bad bots’ to carry out review bombing. In review bombing, attackers threaten to ruin a company’s reputation by posting bad reviews online unless they agree to pay a ransom. CheapAir was attacked by a hacker group in a similar manner. Hackers threatened to post thousands of bad reviews online using automated cyber attacks, such as review bombing, until CheapAir executives accept their demands.
Cybercriminals are also targeting chatbots for stealing critical information by infiltrating them with malware. For instance, hackers have stolen customer payment data from Delta Air Line and Sears by attacking a third-party chatbot provider. Hackers can also develop specialized chatbots with the sole purpose of retrieving sensitive information from users. Denial of inventory bad bots can mainly attack e-commerce websites. Such bots will place multiple products in online shopping carts making them unavailable to buyers. Looking at the shortage of items, customers may visit another e-commerce website for purchasing products.
3. Malware
Hackers are developing new, stealthier forms of malware at a staggering rate. In 2018, cybercriminals had built 856.62 million malware and sources predict that the number will rise to 857.95 million in 2019. The advent of advanced technologies such as machine learning is helping hackers create more intelligent malware. Cybercriminals can now create advanced malware strains that are undetected by cybersecurity systems and spread across an organization’s network. Such malware can stay within an organization’s system for months to find security loopholes and identify normal software and network behavior. After carefully analyzing cybersecurity protocols of the organization, the malware can launch automated cyber attacks on its systems in the most effective manner.
Machine learning-based malware can also target specific people in an organization. For instance, researchers demonstrated a malware called DeepLocker using WannaCry ransomware. The malware had infiltrated a video-conferencing app that scans the faces of several people in the organization using a webcam. After detecting a specific person, DeepLocker launched an automated cyber attack. Such automated cyber attacks can be used to target a specific demographic of people using face, voice, or geolocation detection.
4. Spear-phishing
According to Symantec’s 2018 Internet Security Threat Report, spear-phishing was the most widely employed infection strategy used by 71% of cybercriminal groups. Now, hackers can develop automated cyber attacks to create more effective spear-phishing emails. Hackers can deploy natural language processing to train their attacks using large volumes of publicly available data from various sources such as social media, news articles, and blogs. Using these techniques, cybercriminals can develop more convincing emails and decrease the workload required for creating and executing spear-phishing attacks. Such automated cyber attacks will be quicker compared to the manual approach of spear-phishing.
The effects of automated cyber attacks threaten several businesses that are dependent on data and digital networks. However, cybersecurity professionals are also deploying machine learning and AI to stay ahead of sophisticated cyber threats. Every organization needs to understand that early adoption of modern technologies such as AI will help them gain an upper hand over cyber threats. Also, hybridization of various cybersecurity tools and the proactive application of such tools might be the most feasible approach at the moment.



Leave your comments
Post comment as a guest