Comments
- No comments found

IoT covers a wide range of industries and products.
Due to its diversity, there are certain IoT challenges in security that must be addressed and overcome immediately.
IoT, or the Internet of Things, is a network of all physical objects or things integrated with software, sensors and other technologies, which connects and allows for an exchange of information and data without human intervention or guidance over the internet. IoT is a very enticing technology, and this is what drives humans to adopt it. On average, in 2022, around 29 billion IoT devices are connected to the internet. However, this technology is not entirely free of challenges. It is very much exposed to security threats, and therefore overcoming these IoT challenges in security is of paramount importance.
There could be various challenges to the security of IoT, such as hijacking, dangers of rogue devices, or more.
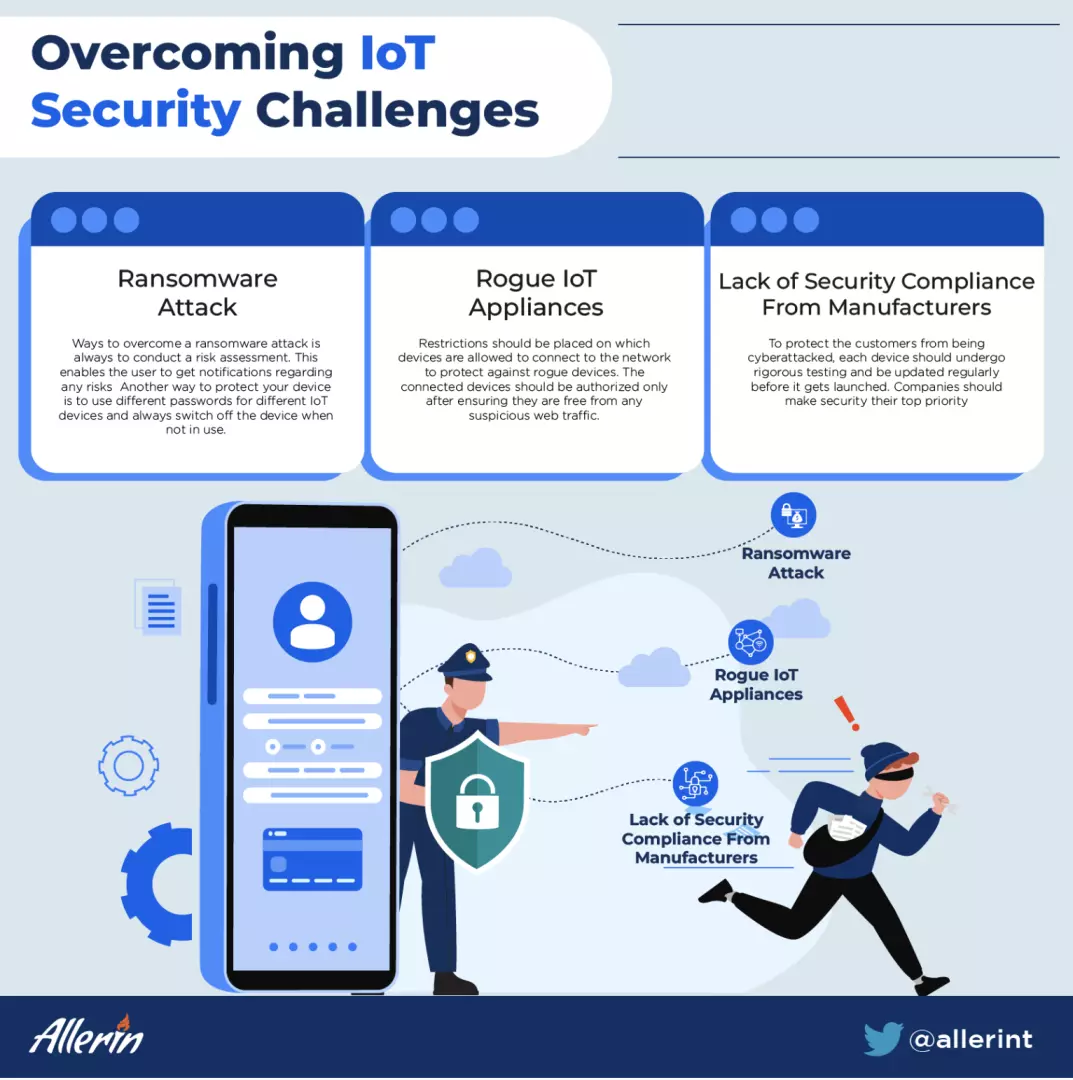
Ransomware is a type of attack that doesn’t destroy sensitive files or data but instead holds the information at ransom and demands money. This attack blocks the user from accessing their files. Around 77% rise in malware attacks in IoT was reported in the current year. IoT devices that have poor security systems, such as smart home products, wearables, etc., are the ones at greatest risk.
Ways to overcome a ransomware attack is always to conduct a risk assessment. This enables the user to get notifications regarding any risks. Another way to protect your device is to use different passwords for different IoT devices and always switch off the device when not in use.
Some employees bring their own IoT devices to the organization. If these devices are not secured, it increases the risk of cyberattacks on the entire organization. Personal devices are the ones that are the easiest to discover by cybercriminals and, in turn, can act as rogue devices and extract confidential information. The enterprise security department isn't always aware of all the devices connected to its networks, which can increase the risk of cyber attacks.
Restrictions should be placed on which devices are allowed to connect to the network to protect against rogue devices. The connected devices should be authorized only after ensuring they are free from any suspicious web traffic.
One of the significant security concerns to IoT devices arises from the source. Any small device, such as a fitness tracker, can expose personal information if the manufacturer lacks compliance. Manufacturers can easily start working on new products without ensuring the safety and security standards of the device in the market.
Therefore, to protect the customers from being cyberattacked, each device should undergo rigorous testing and be updated regularly before it gets launched. Companies should make security their top priority.
IoT technology is ever evolving and getting adopted all around the world. It is being used in every sphere of life; hence, we must ensure that our security systems are up to the standard to protect the devices against any threats and other IoT challenges in security.
Naveen is the Founder and CEO of Allerin, a software solutions provider that delivers innovative and agile solutions that enable to automate, inspire and impress. He is a seasoned professional with more than 20 years of experience, with extensive experience in customizing open source products for cost optimizations of large scale IT deployment. He is currently working on Internet of Things solutions with Big Data Analytics. Naveen completed his programming qualifications in various Indian institutes.
Leave your comments
Post comment as a guest