Comments
- No comments found

Zero trust cybersecurity is increasingly being adopted as a way to improve cybersecurity in organizations of all sizes and industries.
The impact of cybercrimes is expected to increase exponentially by 2025 and reach an estimated $10.5T. In CY 2022 cybersecurity breaches had a global economic impact evaluated at $6T and the average cost reported per cybersecurity breach was $4.35M. Investors have recognized the need and potential of this mega-industry which is equivalent to a nation’s GDP and larger than most country’s GDPs. We have witnessed an increase in venture capital , private equity and overall mergers and acquisitions, as well as a vibrant startup ecosystem offering a complex range of cyber-defense solutions.
Zero-trust cybersecurity is a security model that assumes that any network, device, or user may be compromised and therefore requires authentication and authorization for access to resources. As outlined by the World Economic Forum (WEF) there is an urgency for governments and business leaders to adopt zero trust cybersecurity in this current global economic and socio-political environment.
The zero-trust approach that encourages us to "never trust and always verify" can help restore digital trust by limiting access to sensitive information and systems to only those who have been verified and authorized, reducing the risk of unauthorized access or data breaches. Additionally, it can also help organizations comply with regulatory requirements and industry standards for data security.
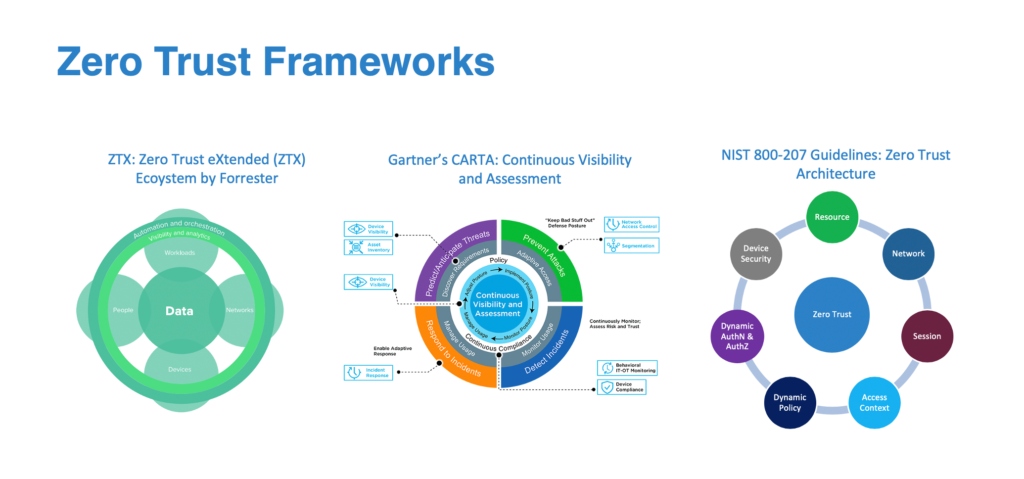
The principles that define a zero-trust architecture are:
All data and services are resources
All communications is secured regardless location
Access to enterprise resources is session based
Access to resources is determined dynamically
Continuous security posture monitoring
Strict authorization and access enforcement
Continuous data collection & enforcement enhancements
Integration with enterprise detection & response
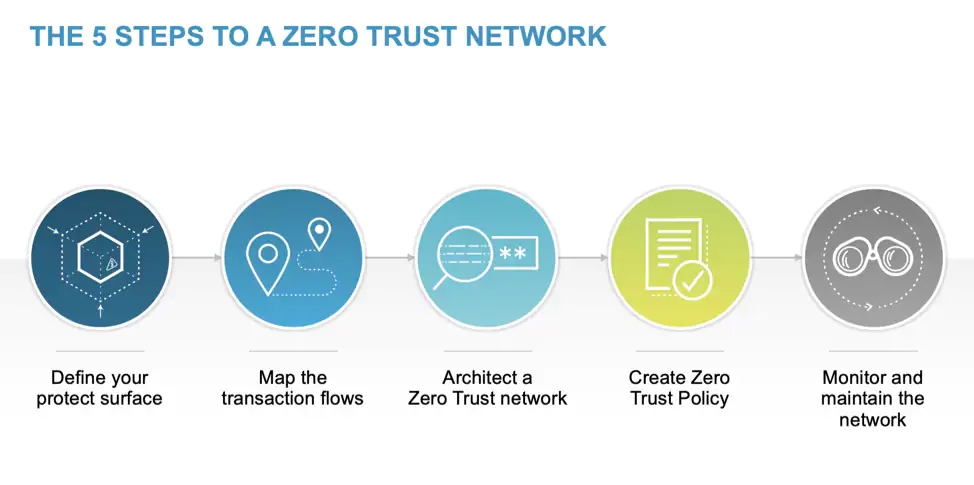
Investing in zero trust cybersecurity can include a variety of different technology solutions and services. Some common investments that organizations may make to implement a zero-trust model include:
Identity and access management (IAM) solutions: These solutions can be used to verify the identity of users and devices and control access to resources based on predefined policies.
Multi-factor authentication (MFA) solutions: These solutions can be used to add an additional layer of security by requiring users to provide multiple forms of authentication before accessing resources.
Network segmentation solutions: These solutions can be used to segment networks and isolate sensitive data and systems from the rest of the network.
Endpoint security solutions: These solutions can be used to protect endpoint devices such as laptops and mobile devices from malware and other threats.
Cloud security solutions: These solutions can be used to secure cloud environments and protect data and systems that are hosted in the cloud.
Security information and event management (SIEM) solutions: These solutions can be used to monitor and analyze security-related data from various sources to detect and respond to threats.
Professional services: Organizations can also invest in professional services such as security assessments, penetration testing, and incident response planning to help identify vulnerabilities and develop a robust security strategy.
The zero-trust cybersecurity investment size and type will depend on the specific needs and requirements of the organization, the size of the organization, as well as the organization’s technological maturity, risk tolerance and results of a robust feasibility analysis.
The impact of zero-trust cybersecurity can vary depending on the specific industry sector and the types of data or systems that are being protected. Examples of implementing a zero-trust model in various industries include:
Government and Defense
Energy (Chevron)
Environment ( Softhread )
Zero-trust cybersecurity architecture, as outlined by the National Institute of Standards and Technology NIST can have a profound impact on data governance, as it can help to secure sensitive data and systems in various industries by verifying the identity of users and devices, and by limiting access to resources based on predefined policies related to regulatory guidelines or specific business rules.
However, there are numerous challenges encountered when deploying zero-trust cybersecurity, such as cost, interoperability, alignment with other enterprise strategic priorities, harmonization with ethics and risk programs, etc.
What can C-suite leaders do to be better prepared for success when planning a zero trust strategy? They can focus on creating a culture of cyber-resilience, which translates into increasing cyber-literacy and cyber-fluency for the general enterprise workforce, and optimize ( via upskilling and reskilling) cyber-specific skills for their technical team. The workforce management efforts should be complemented with a proactive digital ethics program deployment and an honest SWAT assessment in the face of increasing sophistication of cyber-attacks globally. Performing a robust FMEA analysis is an imperative for companies that wish to retain or gain competitive advantage. Evaluating and examining existing internal enterprise cyber-capabilities, versus the option to forge strategic partnerships or perhaps scout out for a potential cyber-acquisition should also be on the agenda. The design and deployment of cyber-metrics is a crucial step that requires alignment with other financial, operational and ethics enterprise dashboard metrics. Last, but certainly not least, forward thinking leaders must embed innovation and continuously improve their cyber-defense program to dynamically adjust to the rapidly evolving cyber landscape.
Futurists envision cyber-resilient programs that will most likely include satellite internet, human-computer interfaces, cyber-digital twins, quantum technology, federated learning, etc.
Globalists and ESG-conscious leaders are hoping that our transition to the next iterations of the world wide web, such as web 3.0 and web 4.0 will have state of the art cyber-defense programs and will align with both the UN SDG 2030, as well as with the net-zero UN 2050 agendas.
Ingrid Vasiliu-Feltes, MD MBA Is a healthcare executive, futurist and globalist who is highly dedicated to digital and ethics advocacy. She is a Forbes Business Council member, digital strategist, passionate educator and entrepreneurship ecosystem builder, known as an expert speaker, board advisor and consultant. Throughout her career she has received several awards for excellence in research, teaching or leadership. She is the recipient of numerous awards most notably: WBAF World Excellence AwardSocial Entrepreneurship 2021, Top 20 Global Leaders in Digital Twins Technologies, Top 50 Global Leaders in Health Tech,Top 50 Global Ecosystem Leaders, Top 100 Visionary In Education Award 2021, Top 100 Global Women in Leadership Award 2021, Top 100 World Women Vision Award, 2021-Innovation & Tech, Top 100 Women in Social Enterprise 2021 (nominee),Top 50 Global Thinkers (Nominee),Nations of Women Change Makers Award(finalist),Top 100 Healthcare Leader 2020 Award, Top 100 Finance Leader 2020 Award, and Top 100 Women in Crypto 2020. Additionally, she serves as an Expert Advisor to the EU Blockchain Observatory Forum, and was appointed to the Board of UN Legal and Economic Empowerment Network. Dr. Vasiliu-Feltes is CEO of Softhread Inc., the Founder and CEO of The Science, Entrepreneurship and Investments Institute, and currently serving as a Country Director for WBAF USA, Senator of WBAF, Faculty Member of the WBAF Business School-Division of Entrepreneurship, and teaching the Executive MBA Business Technology Course at the UM Business School. She is also acting as the Chief Innovation Officer for the Government Blockchain Association. Most recently she served as President of Detect Genomix, Chief Quality and Safety Officer Chief and Innovation Officer for Mednax, Chief Quality and Safety Officer and Chief of Compliance for the University of Miami UHealth System During her academic tenure she taught several courses within the Medical School, as well as the combined MD/PhD and MD/MPH programs. Throughout her career, Dr. Vasiliu-Feltes held several leadership positions and is a member of numerous prestigious professional organizations. She holds several certifications, such as Bioethics from Harvard, Artificial Intelligence and Business Strategy from MIT Sloan, Blockchain Technology and Business Innovation from MIT Sloan, Finance from Harvard Business School, Negotiation from Harvard Law School, Innovation and Entrepreneurship from Stanford Graduate School of Business, Certified Professional in Healthcare Risk Management, Fellow of the American College of Healthcare Executives, Patient Safety Officer by the International Board Federation of Safety Managers, Master Black Belt in Lean and Six Sigma Management, Professional in Healthcare Quality by the National Association of Healthcare Quality, Manager for Quality and Organizational Excellence, by the American Society for Quality, and Certified Risk Management Professional by the American Society for Healthcare Risk Management. Additionally, Dr. Vasiliu-Feltes is an Honorary Advisory Board Member of several companies, as well as an Editorial Board Member for several international publications, an author and TV/Media partner.
Leave your comments
Post comment as a guest