Comments
- No comments found

The term ‘Zero Trust’ has garnered significant attention and endorsement from the security industry to government administrations alike, with a simple Google search immediately finding some 2,900,000,000 results.
But with seemingly everyone from NIST to the NSA recommending Zero Trust, what exactly is it? I would argue the meaning has become ambiguous, confused and even distorted which can lead to serious risk consequences if a business believes it can simply buy a ‘zero trust solution’ off the shelf and be ‘once and done’.
‘You do not flip a switch or take a pill to ‘become’ zero trust, it is not something you can simply install or buy from a single vendor - this is an ongoing journey and not a destination’
A Zero Trust approach therefore necessitates a continual focus, shared responsibility and embedded reflection to take stock of where to start, what’s working, what isn’t, and where to go to next. Let’s explore how we reached this point and the key components of the practice and not the product of Zero Trust today - and to help organizations bake-in readiness for the constant evolution of Cyber Security risk considerations well into the future too.
Necessity breeds innovation and accelerated by the pandemic, business today has forever changed with the global advance of data-driven digital transformation and application development modernisations at both speed and scale. This has heralded the rise of multi-cloud adoption and cloud-native applications, an increasingly API economy, an IoT device explosion, emergent technology integration notably across AI, Cloud and 5G disciplines and increased IT/OT convergence. The advance of hybrid distributed working and broadened digital and technological adoption has also catalysed an evolution in consumer and employee behaviours - alongside heightened experience expectations across web, app, social app and developer tools too.
We have also seen new levels of public awareness around issues of data breaches and security, privacy and compliance issues, alongside a renewed consciousness around values and purpose across Diversity, Equity, Inclusion and also Environmental, Social and Governance (ESG) perspectives. So much so, that ultimately questions of trust do take on a broader contextual meaning. With businesses now more trusted than governments and even NGO’s as evidenced by the Edelman Trust Barometer 2021, ‘getting Trust right’ has probably never mattered more, even becoming a competitive advantage differentiator, especially for sensitive areas like security.
‘Continual commitment to Chasing Zero Trust will ultimately earn you customer trust!’
Accompanying this change, the cybersecurity threat landscape has also transformed - becoming ever more converged, complex and sophisticated. The leading threats to organizations are ransomware and phishing, with zero day attacks, exploits via SaaS platforms, Log4j, DoS DDoS and MitM attacks, IoT and supply chain vulnerabilities, Cloud Washing, device hacking and misconfiguration, and moreover the rise of bring your own device (BYOD) to support a ‘work from anywhere’ distributed culture all leading concerns.
Equally we are seeing bad actor collaboration, attacks moving beyond hitting critical infrastructure to mundane infrastructure, and a myriad of examples of expanding threat vectors, including remote code execution (RCE), workload-focused ransomware attacks and lateral movements inside and across clouds and within data centres where east-west traffic has become the new battleground. This combination of heightened risk alongside endpoint choice, flexible workstyles and applications everywhere means that the once traditional, established trust boundaries that use perimeter security simply no longer exist. Endpoints are not “yours” anymore.

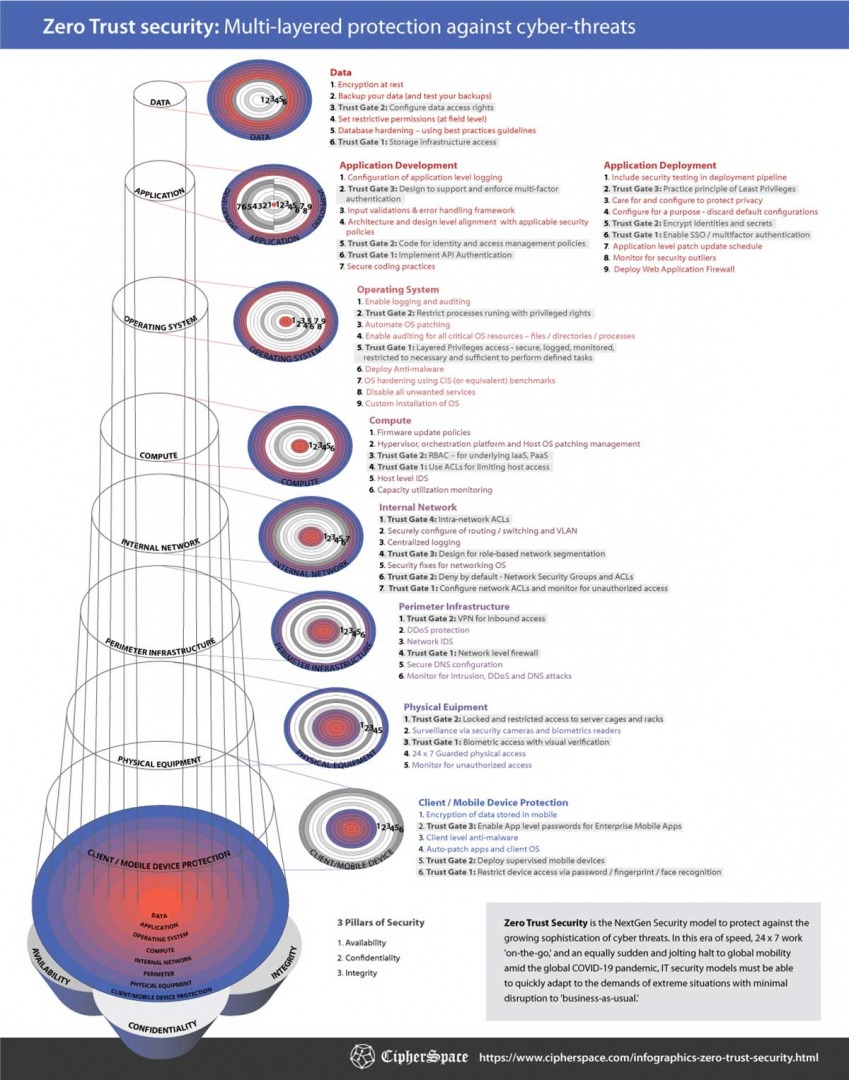
Practicing Zero Trust does not require organizations to completely ‘rip out their current security controls’ and start totally anew (Forrester 2021), rather you can optimise existing investments and maturity levels, complemented by additional aligned security technology and platforms where appropriate, alongside proper planning, training and education culture, and staffing. Zero Trust is a security approach for which multiple types of technologies must be implemented across different vectors to achieve the end goal of holistic end-to-end security, minimizing implicit trust.
So what does this practice look like and how do we address the challenges identified? There are 3 core pillars to establishing an ongoing and end-to-end Zero Trust architecture: Continual Verification, Moving Beyond Users to Workloads, and Security Operations Evolution.
Perhaps ‘Zero Assumptions’ is the best place to start - we must assume nothing! Applying least privilege is not enough - implementing Zero Trust demands verification of each and every access, request for an application, privacy elevation etc - whether the source is external or internal to the network. Or in other words, it necessitates embedding an architecture of continual verification that ensures access is secure, authenticated, and authorized every time, reducing the attack threat surface wherever possible. In addition, another perspective on verification (or certification) can be considered at the device access level itself – this means going back to the root of trust and building on trusted components. A fundamental aspect of IoT security today is the very components with which devices are built (PSA Certified 2022).
Expanding the Zero Trust focus from Users to Workloads is a modern business imperative – this is where many of the leading cybersecurity battles are being contended and moreover being fought in runtime. When workloads are compromised, attackers are able to move laterally across web, app and database servers, and this is when significant damage can be incurred. The need to expand Zero Trust to consider ‘more than just users’ is further reinforced by the impact of Web3 as users are inherently authenticated. In Part 2 of this series, we explore the how of Secure Workload Access, notably East-West Cloud and Cloud-to-Cloud Edge controls using techniques including Micro segmentation, API Security, Advanced Threat Prevention, Workload Security and Edge Security.
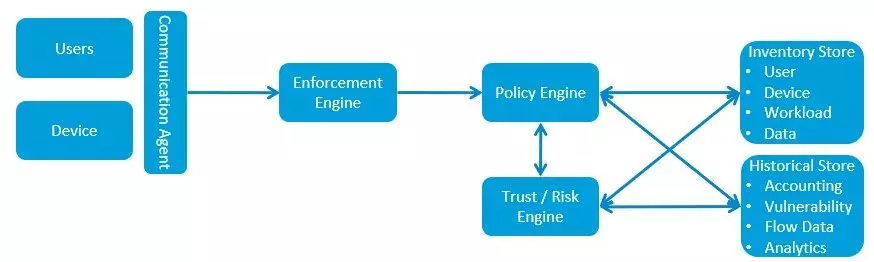
Increasingly distributed IT infrastructures coupled with the escalation of cyber security threats means that the people driving Security Operations are often faced with resource pressures, risk of burnout, navigating disparate tools and facing alert overload all at the same time. This raises a pressing need to provide the ‘power to empower’ and move from reactive and silo-ed, to active, integrative and real-time intelligence, which also frees up time for higher order work activities by staff improving productivity and reducing stress and churn too. And as we will explore in Part 2, this can be actualised through end to end visibility and orchestration tools, with as much context as possible, all supported by a high degree of automation – this heralds the modernisation of the Security Operations Centre – the SOC 4.0.
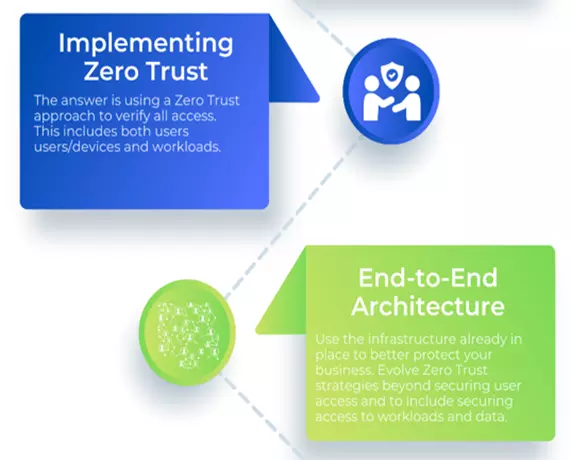
We have seen that embedding a distributed security architecture that protects users, data, apps and workloads right across the network from endpoints to the data centre and across multiple clouds can greatly support the continual practice of Zero Trust security. It is equally clear that our approach to change must evolve too, borrowing the analogy and mindset of Continuous Integration, Continuous Deployment (CI-CD) used in agile iterative change management, so we must have the responsive architecture in place to constantly evolve to ever transforming, expanding and converging Cyber Security threats.
And this practice is never ‘once and done’. It is not something you ever finish. Rather it is an ongoing journey that can be non-linear and must evolve as you do - bringing together technology, process, people, culture, skills and shared responsibility – whilst creating shared value too. In the next piece we consider the roadmap to embracing Zero Trust end-to-end in more detail – join us on the journey, all feedback welcome!
Dr. Sally Eaves is a highly experienced chief technology officer, professor in advanced technologies, and a Global Strategic Advisor on digital transformation specializing in the application of emergent technologies, notably AI, 5G, cloud, security, and IoT disciplines, for business and IT transformation, alongside social impact at scale.
An international keynote speaker and author, Sally was an inaugural recipient of the Frontier Technology and Social Impact award, presented at the United Nations, and has been described as the "torchbearer for ethical tech", founding Aspirational Futures to enhance inclusion, diversity, and belonging in the technology space and beyond. Sally is also the chair for the Global Cyber Trust at GFCYBER.
Dr. Sally Eaves is a highly experienced Chief Technology Officer, Professor in Advanced Technologies and a Global Strategic Advisor on Digital Transformation specialising in the application of emergent technologies, notably AI, FinTech, Blockchain & 5G disciplines, for business transformation and social impact at scale. An international Keynote Speaker and Author, Sally was an inaugural recipient of the Frontier Technology and Social Impact award, presented at the United Nations in 2018 and has been described as the ‘torchbearer for ethical tech’ founding Aspirational Futures to enhance inclusion, diversity and belonging in the technology space and beyond.
Leave your comments
Post comment as a guest