Comments
- No comments found
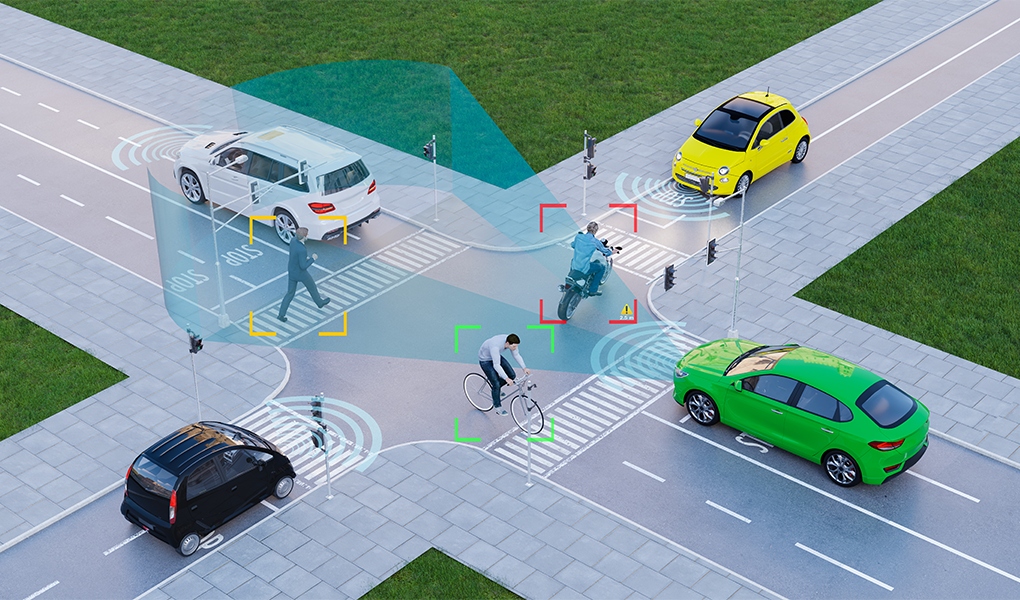
As cyber threats continue to evolve in sophistication, the need for robust defense mechanisms is paramount.
Enter computer vision, a cutting-edge technology that is revolutionizing the way we protect our digital assets. The digital realm is constantly under siege from an array of cyber threats. Malware, phishing attacks, ransomware, and data breaches have become daily headlines, causing financial losses and reputational damage to individuals and organizations alike.
One of the greatest challenges in cybersecurity is the human factor. Social engineering attacks, where hackers exploit human psychology to gain unauthorized access, are on the rise. Traditional security measures, while effective to a certain extent, are often inadequate in dealing with these evolving threats.
Computer vision is a field of artificial intelligence (AI) that empowers computers to interpret and understand visual information from the world. It allows machines to "see" and make sense of the visual data they capture.
While computer vision initially gained prominence in areas like facial recognition and image classification, its applications have expanded far beyond. It now plays a pivotal role in enhancing cybersecurity measures.
Computer vision systems can monitor network traffic and analyze patterns in real-time. They can detect unusual or suspicious activities, such as unauthorized access or data exfiltration, and trigger immediate responses.
By analyzing user behavior and activity patterns, computer vision can identify anomalies and deviations from typical user interactions. This helps in detecting insider threats and potential security breaches.
Facial recognition technology, driven by computer vision, can be used for multi-factor authentication. It adds an extra layer of security by ensuring that only authorized individuals gain access to sensitive systems or data.
Computer vision can visualize security events through graphical representations, making it easier for security professionals to comprehend complex data and respond swiftly to threats.
Computer vision is transforming traditional video surveillance into intelligent systems. These systems can automatically identify and track individuals, vehicles, or objects of interest, providing real-time alerts for security breaches.
By analyzing employees' digital behavior, computer vision can identify potential insider threats, such as employees attempting to access sensitive information without authorization.
Computer vision can analyze email content and identify phishing attempts by recognizing suspicious patterns or anomalies in the text and attachments.
Machine learning algorithms powered by computer vision can analyze code and detect subtle variations or anomalies in software, making it easier to identify new strains of malware.
The use of computer vision in cybersecurity raises privacy concerns, particularly in facial recognition. Striking a balance between security and privacy is crucial.
Machine learning models used in computer vision can inherit biases present in their training data, leading to discriminatory outcomes. Efforts to mitigate bias are ongoing.
The storage and processing of visual data for cybersecurity purposes must adhere to stringent data privacy regulations to protect individuals' rights.
The future holds the promise of autonomous cybersecurity systems powered by computer vision. These systems will not only detect threats but also respond and adapt to evolving cyberattacks in real-time.
Machine learning algorithms will work in tandem with cybersecurity experts, providing them with valuable insights and recommendations for decision-making.
Facial recognition and other biometric authentication methods driven by computer vision will become more widespread, replacing traditional passwords and PINs.
The integration of computer vision into cybersecurity is a game-changer in our ongoing battle against cyber threats. It empowers us to detect, analyze, and respond to security incidents with greater efficiency and accuracy. However, as this powerful technology continues to evolve, ethical considerations and privacy concerns must remain at the forefront of its implementation. Striking the right balance between security and individual rights is essential as we harness the capabilities of computer vision to safeguard our digital realm. The future of cybersecurity is undoubtedly being shaped by the vigilant gaze of computer vision, ensuring a safer and more secure digital world for all.
Naveen is the Founder and CEO of Allerin, a software solutions provider that delivers innovative and agile solutions that enable to automate, inspire and impress. He is a seasoned professional with more than 20 years of experience, with extensive experience in customizing open source products for cost optimizations of large scale IT deployment. He is currently working on Internet of Things solutions with Big Data Analytics. Naveen completed his programming qualifications in various Indian institutes.
Leave your comments
Post comment as a guest