Comments
- No comments found

Artificial intelligence, machine learning, IoT, 5G and big data will help cybersecurity leaders make better decisions in 2025.
When asked about what 2025 looks like, some people fear it will bring a greater divide between the haves and the have-nots.
The culprit? Pew Research points to technology companies amassing greater power through big data, surveillance, privacy invasion and the power of social media to spread both useful facts and misinformation.
Cybersecurity plays a leading role in how the future plays out. In an article published by Pew Research Center entitled “Worries About Life in 2025,” authors Janna Anderson, Lee Rainie and Emily A. Vogels write: “Many warned that health-monitoring, work-surveillance and security solutions that may be applied will expand mass oversight, threaten human rights and lead more regions of the world to become more authoritarian.”
What will be the role of cybersecurity leaders in a world where the very security solutions they employ are both viewed as a benefit and a potential risk?
I see the cybersecurity role of the future crossing present-day boundaries and leadership circles. It will be part steward of an organization and part protector. It will be everywhere and impact everyone.
I also believe cybersecurity leaders will have a tremendous impact on the culture of an organization because – as the old saying goes – we are only as strong as the weakest link. Everyone within an organization contributes to security. That perhaps is the biggest change between the present landscape and how cybersecurity leadership will evolve by 2025 and beyond.
We may see cybersecurity culture directors who rally for both employee and executive support in protecting and enhancing the brand and customer experience as well as hardware and data. Priorities will shift too. Cybersecurity leaders will “own” revenue-generating responsibilities, contribute to strategic vision, manage expectations as innovative technologies like AI roll out, and help develop new technology roles that don’t even exist yet.
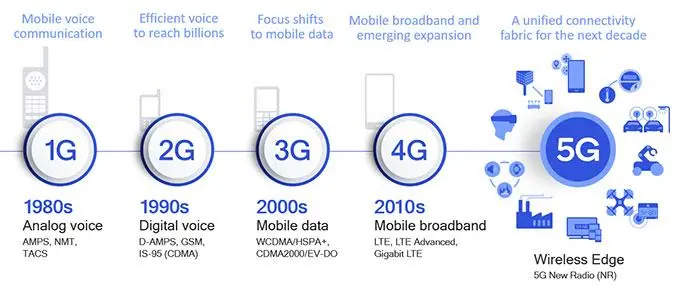
I remember hearing this advice when I was younger: always keep one eye on the present and one on the future. The path to 5G is the future, and it is unfolding faster than experts predicted because of rising competition among communications service providers (CSPs). Equally telling, Gartner predicts that 40% of boards will have a “dedicated cybersecurity committee overseen by a qualified board member” by 2025.
As a board member myself, I can truthfully say that when boards stand up and take note of a business function, you know a change is far more than a trend; it’s here to stay.
One major driver of 5G is AT&T, which produced its tenth annual report on the topic. The 36-page AT&T Cybersecurity Insights™ Report: 5G and the Journey to the Edge is available at no cost, except for handing over your email. The information within is well worth the exchange. Here are my top takeaways:
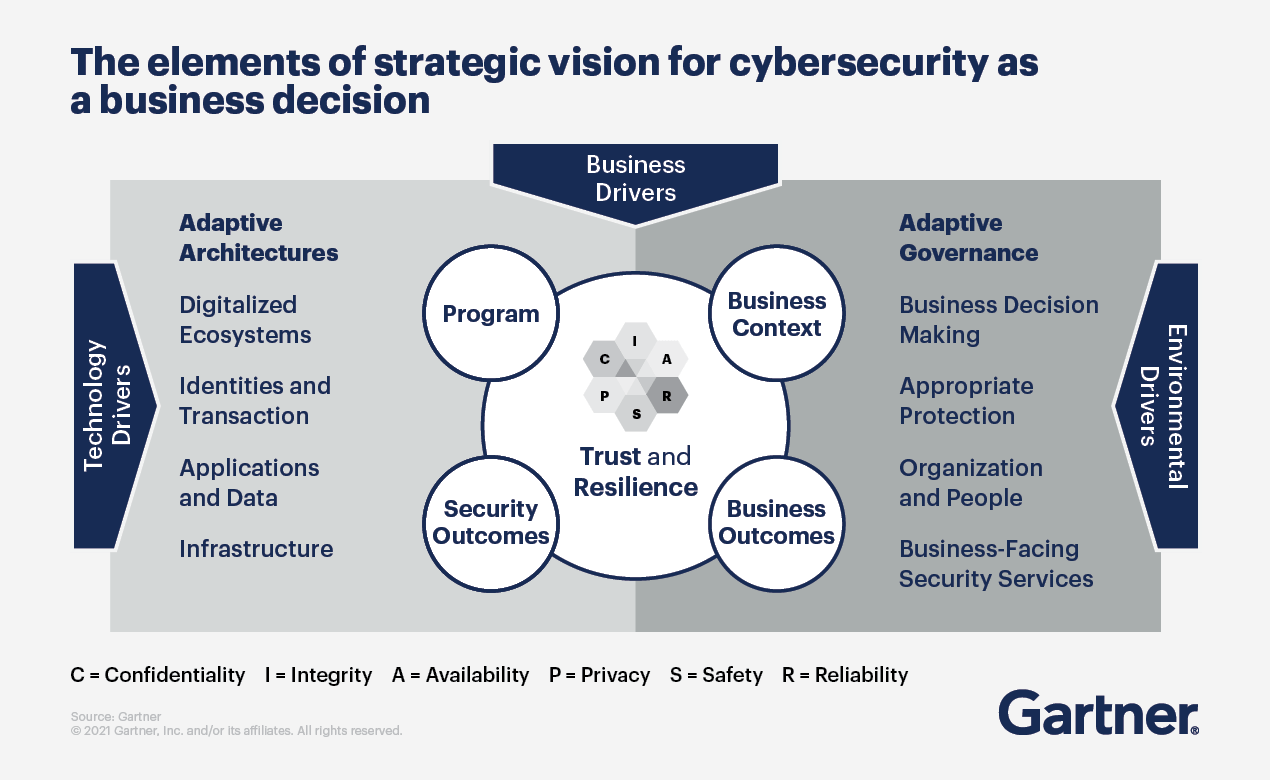
Progress often creates new risks. While 5G offers speed, lower latency and greater capacity to do more, it also opens a Pandora’s box for cybersecurity leaders with an increase of unsecured IoT devices, data, and remote workers using their own technology all converging to create a larger attack surface. In reality, there are simply more places and spaces to infiltrate for cybercriminals who are, unfortunately, just as savvy at building code and problem-solving as the good guys.
No doubt, the cyber threat landscape will continue to evolve. For example, there will be a shift in IoT priorities to the “security of things” and the “identity of things” over the next two to five years. Here again, AT&T Cybersecurity, the company’s solution to protecting organizations and helping them inspire customer trust and innovation, provides a wealth of insight. Through consultants (yes, real human beings who can answer real questions), managed security services and global threat intelligence (via AT&T AlienLabs), AT&T helps companies of all sizes identify risks and respond to attacks.
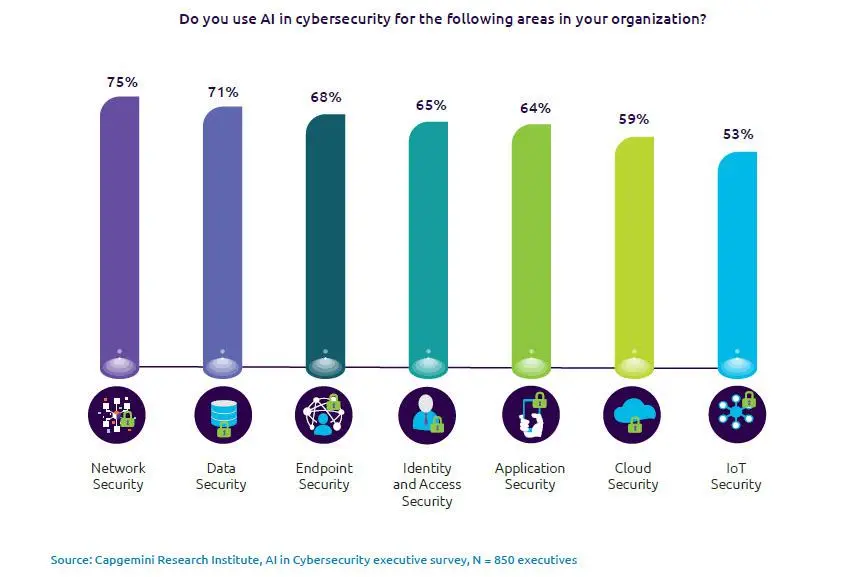
How can emerging cognitive technologies – such as AI, ML, automated networks and Cloud – help companies navigate an increasingly treacherous landscape?
Experts are split on the answer. IEEE looked at this topic in an article entitled “The Impact of AI on Cybersecurity.” Author Eddie Segal writes: “AI, machine learning, and threat intelligence can recognize patterns in data to enable security systems to learn from past experience.” This, is good, except it also implies a breach has to happen first for AI to learn from past mistakes. Also, AI is expensive and may be cost-prohibitive for small and midsize companies. However, the article points out that AI can “enhance the threat hunting process” and “reduce the cost of hardware maintenance by alerting when you have to fix the equipment.”
The cybersecurity leader’s list of priorities will continue to adapt to new cyber-threats, viruses and issues that may be unimaginable today. However, those who are open to learning, sharing knowledge and integrating cybersecurity into their business strategy and culture will win. Here, we borrow a few words of wisdom from the Director of Cyber Operations at Cardinal Health, Britney Hommertzheim: “As cybersecurity leaders, we have to create our message of influence because security is a culture and you need the business to take place and be part of that security culture.”
Cybersecurity leaders no longer fit in a neat box labeled IT professionals. They are strategists fueling the future of an organization’s success starting right now, right this moment.
This post was sponsored by AT&T Business, but the opinions are my own and don’t necessarily represent BBN Times and AT&T Business’s positions or strategies.
Helen Yu is a Global Top 20 thought leader in 10 categories, including digital transformation, artificial intelligence, cloud computing, cybersecurity, internet of things and marketing. She is a Board Director, Fortune 500 Advisor, WSJ Best Selling & Award Winning Author, Keynote Speaker, Top 50 Women in Tech and IBM Top 10 Global Thought Leader in Digital Transformation. She is also the Founder & CEO of Tigon Advisory, a CXO-as-a-Service growth accelerator, which multiplies growth opportunities from startups to large enterprises. Helen collaborated with prestigious organizations including Intel, VMware, Salesforce, Cisco, Qualcomm, AT&T, IBM, Microsoft and Vodafone. She is also the author of Ascend Your Start-Up.
Leave your comments
Post comment as a guest